This is another dose of bug bounty tips from the bug hunting community on Twitter, sharing knowledge for all of us to help us find more vulnerabilities and collect bug bounties.
This is the 4th part and in each part we are publishing 10 or more tips. Here we go..
- 1. Price manipulation methods
- 2. Find javascript files using gau and httpx
- 3. Extract API endpoints from javascript files
- 4. Handy extension list for file upload bugs
- 5. Access Admin panel by tampering with URI
- 6. Bypass 403 Forbidden by tampering with URI
- 7. Find database secrets in SVN repository
- 8. Generate content discovery wordlist from URI
- 9. Extract endpoints from APK files
- 10. A recon tip to find more subdomains (Shodan)
- 11. Find hidden GET parameters in javascript files
- 12. GitHub dorks for finding sensitive information
- 13. Bypass Rate limits by adding X- HTTP headers
- Conclusion
1. Price manipulation methods
By @lutfumertceylan, @y_sodha, @SalahHasoneh1
Source: link1, link2, link3
Here’s not 1, but 3 tips on how to manipulate with prices in web applications.
Method #1:
- If the product price parameter cannot be changed, change the quantity of products:
- items[1][quantity]= 1 –> 234 EUR
- items[1][quantity]= 0.1 –> 23.4 EUR
- Congratulations, you bought the order for 10% of the price!
Method #2:
- Add 2 products to the basket – let’s consider a single product is $40
- If the request is processed in this way:
{“items”:{“laptop”:1,”mobile”:1}} - Change the JSON body to:
{“items”:{“laptop”:4,”mobile”:-2}} - The cost will become $20 for 2 items:
4 * $40 – 2 * $70 = $160 – $140 = $20
Method #3:
- Select any item to purchase
- Select PayPal as a payment method, intercept all the requests
- Until you got a parameter called ‘amount’ from PayPal
- Manipulate with the price and change it to 0.01$
- Pay, and wait for the confirmation
2. Find javascript files using gau and httpx
Here’s a recon tip to find javascript files hosted on our target using gau and httpx utilities:
echo target.com | gau | grep '\.js$' | httpx -status-code -mc 200 -content-type | grep 'application/javascript'What this combo will do is that it will collect all known URLs for our target from the AlienVault’s Open Threat Exchange (OTX), the Wayback Machine and Common Crawl, fetch them using httpx and then display only javascript files.
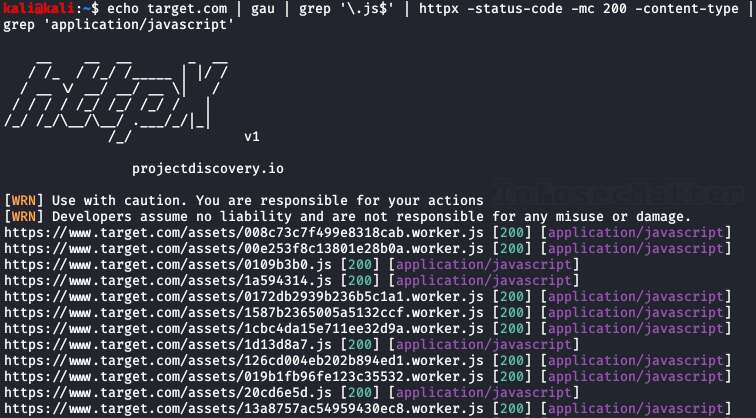
In order for this combo to work, we have to install the following tools:
3. Extract API endpoints from javascript files
By @renniepak
Source: link
Here’s a quick one-liner for extracting API endpoints from javascript files:
cat file.js | grep -aoP "(?<=(\"|\'|\`))\/[a-zA-Z0-9_?&=\/\-\#\.]*(?=(\"|\'|\`))" | sort -u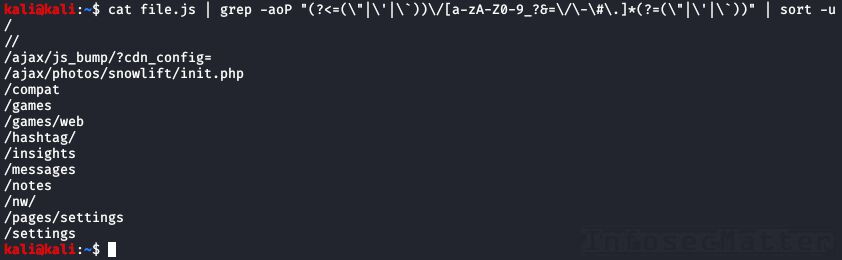
Very useful!
4. Handy extension list for file upload bugs
By @pwntheweb
Source: link
The following file extension lists can be useful when we are trying to find vulnerabilities in file upload functionalities:
ASP:
- .aspx
- .config
- .ashx
- .asmx
- .aspq
- .axd
- .cshtm
- .cshtml
- .rem
- .soap
- .vbhtm
- .vbhtml
- .asa
- .asp
- .cer
- .shtml
PHP:
- .php
- .php5
- .php3
- .php2
- .shtml
- .html
- .php.png
(double extension attack)
What we would typically want to achieve is to circumvent the controls restricting the type of content that can be uploaded onto the website and try to upload something interesting like:
- ASP / PHP file with a webshell – RCE
- HTML file with Javascript code – XSS
- EICAR file – test possibility of hosting malware
Protip: Don’t forget to always try the NULL byte injection trick as well, e.g.:
- file.jpg%00shell.php
- shell.php%00file.jpg
- shell.php%00.jpg
5. Access Admin panel by tampering with URI
By @SalahHasoneh1
Source: link
Here’s a super easy tip to access an admin panel by tampering with the URI in the following way:
- https://target.com/admin/ –> HTTP 302 (redirect to login page)
- https://target.com/admin..;/ –> HTTP 200 OK
Try also the following tips, as others have commented on the tweet:
- https://target.com/../admin
- https://target.com/whatever/..;/admin
6. Bypass 403 Forbidden by tampering with URI
This tip is very similar to the previous one. By tampering with the URI we might be able to bypass access controls of the application:
- site.com/secret –> HTTP 403 Forbidden
- site.com/secret/ –> HTTP 200 OK
- site.com/secret/. –> HTTP 200 OK
- site.com//secret// –> HTTP 200 OK
- site.com/./secret/.. –> HTTP 200 OK
It’s rare to see, but there’s no loss to give it a shot.
Update: The author posted an update to advise on using more comprehensive and workflow oriented approach such as the 403 Bypass guide (Github).
Note that today there are also automated tools for bypassing 403 Forbidden errors, see e.g. newer bug bounty tip BBT10-7 – Automated 403 Forbidden bypasser tools.
7. Find database secrets in SVN repository
By @faizalabroni
Source: link
Here’s how @faizalabroni was able to discover database secrets in SVN repository and collect bug bounty:
- Run
./dirsearch.py -u target -e php,html,js,xml -x 500,403 - Found http://url.com/.svn/
- Clone & use SVN-Extractor
- Run
./svn-extractor.py --url http://url.com --match database.php - Result in output dir and just open it
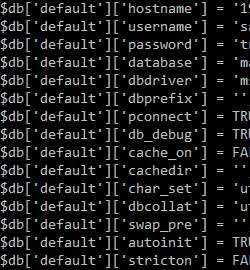
Instant bounty!
Here’s the list of tools we need for this tip:
8. Generate content discovery wordlist from URI
By @healthyoutlet
Source: link
There’s a useful tool called sprawl to expand a list of URI paths, e.g. from waybackurls or gau, and generate a content discovery wordlist. Here’s how to use it:
echo '/1/dev/admin' | python3 sprawl/sprawl.py -s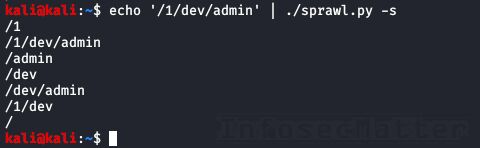
Now we could use this wordlist to discover additional endpoints hosted on our target.
The tool lives here:
9. Extract endpoints from APK files
By @SalahHasoneh1
Source: link
Another useful tool for analyzing Android APK files is apkurlgrep made by @delphit33. This tool can extract URL from an APK file without even needing to unpack it first.
apkurlgrep -a path/to/file.apkGet the tool from here:
10. A recon tip to find more subdomains (Shodan)
Big companies often use their own CDN (Content Delivery Network) and some of them are used to serve internal static files such as javascript files.
Using the following steps we can find additional internal subdomains and juicy javascript files via Shodan search engine:
- Do a passive or active enumeration of the CDN domain, e.g. bigcompanycdn.com
- For whatever subdomains found, search that on Shodan using the “http.html” filter
- Example: You found dev-int.bigcompanycdn.com, Shodan query will look like this:
- http.html:”dev-int.bigcompanycdn.com”
- http.html:”https://dev-int-bigcompanycdn.com”
11. Find hidden GET parameters in javascript files
By @chiraggupta8769 (@intigriti, @sratarun)
Source: link
Here’s an interesting tip for finding hidden parameters by analyzing javascript files:
- Scour javascript files for variable names, e.g.:
var test = "xxx" - Try each of them as a GET parameter to uncover hidden parameters, e.g.:
https://example.com/?test=”xsstest
This often results in XSS!
Turns out @sratarun made this intricate one-liner generator which finds all variable names and appends them as parameters:
assetfinder example.com | gau | egrep -v '(.css|.png|.jpeg|.jpg|.svg|.gif|.wolf)' | while read url; do vars=$(curl -s $url | grep -Eo "var [a-zA-Z0-9]+" | sed -e 's,'var','"$url"?',g' -e 's/ //g' | grep -v '.js' | sed 's/.*/&=xss/g'); echo -e "\e[1;33m$url\n\e[1;32m$vars"; done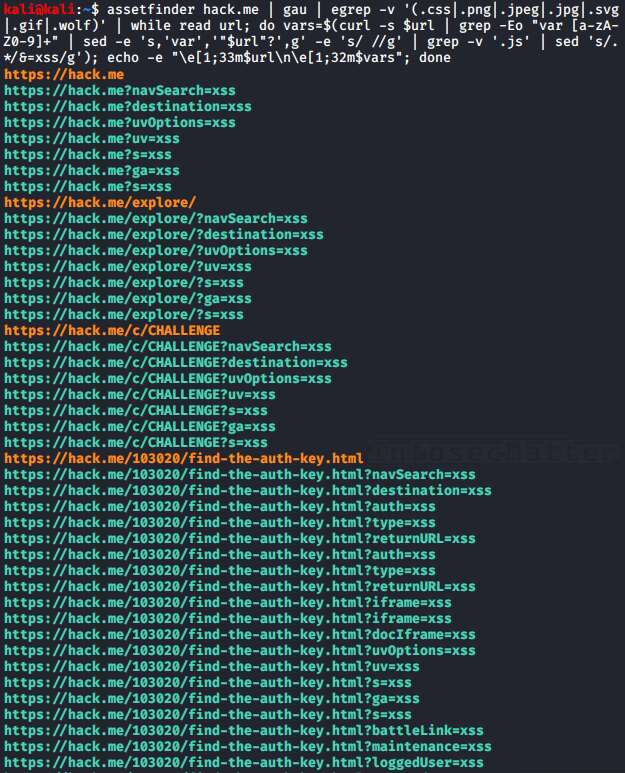
Now we can test all these URLs and check whether we can trigger XSS with them or similar things.
Get all the tools for this tip from here:
12. GitHub dorks for finding sensitive information
By @D0cK3rG33k
Source: link
This is a list of 10 useful GitHub dorks to identify sensitive information using file extensions:
- extension:pem private
- extension:ppk private
- extension:sql mysql dump password
- extension:json api.forecast.io
- extension:json mongolab.com
- extension:yaml mongolab.com
- extension:ica [WFClient] Password=
- extension:avastlic “support.avast.com”
- extension:js jsforce conn.login
- extension:json googleusercontent client_secret
With these GitHub dorks we can identify things like certificate private keys, puttygen private keys, MySQL dumps with passwords, API keys and secrets, MongoDB credentials in json or yaml configs, OAuth credentials for accessing Google APIs and similar sensitive data.
Protip: check also the following repository of GitHub dorks maintained by @techgaun:
13. Bypass Rate limits by adding X- HTTP headers
By @Cyb3rs3curi_ty
Source: link
Here’s a tip to bypass rate limiting load balancers, proxies and WAFs that are in between somewhere on the way to our target.
Add the following HTTP header(s) with your requests:
- X-Originating-IP: IP
- X-Forwarded-For: IP
- X-Remote-IP: IP
- X-Remote-Addr: IP
- X-Client-IP: IP
- X-Host: IP
- X-Forwared-Host: IP
These headers are typically used by intermediate components such as load balancers or proxies and by adding an arbitrary internal IP address in these HTTP headers, we may actually bypass the enforced rate limits.
Try it with IP addresses from the following ranges:
- 192.168.0.0/16
- 172.16.0.0/12
- 127.0.0.0/8
- 10.0.0.0/8
Once we experience a blockage again, simply increment the provided IP address.
This tip may not always work, but is definitely worth to try when things get difficult.
Conclusion
That’s it for this part of the bug bounty tips.
Big thanks to all the authors for sharing their tips:
- @lutfumertceylan
- @y_sodha
- @SalahHasoneh1
- @pdnuclei
- @renniepak
- @pwntheweb
- @remonsec
- @faizalabroni
- @healthyoutlet
- @krizzsk
- @chiraggupta8769
- @intigriti
- @sratarun
- @D0cK3rG33k
- @Cyb3rs3curi_ty
Make sure to follow them on Twitter to stay ahead of the bug bounty game.
SHARE THIS




















