Accessing Windows Systems Remotely From Linux
This page contains a collection of methods for connecting to a remote Windows system from Linux and examples of how to execute commands on Windows machines remotely from Linux using number of different tools. It covers over 30 different methods ...
Metasploit Auxiliary Modules (Detailed Spreadsheet)
On this page you will find a comprehensive list of all Metasploit auxiliary modules that are currently available in the latest Metasploit Framework, the most popular penetration testing platform. I'm hoping that this list will help you navigate through the ...
List of Metasploit Payloads (Detailed Spreadsheet)
On this page you will find a comprehensive list of all Metasploit payloads that are currently available in the open source version of the Metasploit Framework, the most popular penetration testing platform. It is my hope that this will help ...
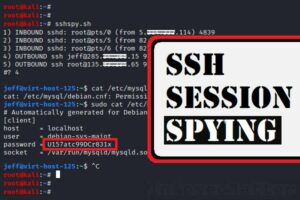
SSH Sniffing (SSH Spying) Methods and Defense
It is well known that SSH is a secure network protocol, inherently safe from network packet sniffing and eavesdropping. This is of course thanks to its use of encryption. If we are using SSH protocol safely, the risks of man-in-the-middle ...
List of Metasploit Windows Exploits (Detailed Spreadsheet)
On this page you will find a comprehensive list of all Metasploit Windows exploits that are currently available in the open source version of the Metasploit Framework, the number one penetration testing platform. It is my hope that this list ...
