Many people ask this question: Can Wireshark capture passwords? Well, the answer is definitely yes! Wireshark can capture not only passwords, but any kind of information passing through the network – usernames, email addresses, personal information, pictures, videos, anything. As long as we are in position to capture network traffic, Wireshark can sniff the passwords going through. But the question is – what kind of passwords? Or more precisely – passwords from which network protocols can we capture? That’s the topic of this article.
- Plain text network protocols
- Capture FTP password
- Capture Telnet password
- Capture SMTP password
- Capture IMAP4 password
- Capture HTTP password
- Capture SNMP community string
- Capture LDAP password
- Capture SOCKS password
- Capture MSSQL password
- Capture PostgreSQL password
- Capture IRC password
- Capture OSPF password
- Capture BFD password
- Capture STUN authentication
- Better approach to capture passwords
- Frequenty asked questions (FAQ)
- Can Wireshark be detected?
- Is Wireshark safe to use?
- Can Wireshark capture packets from other computers?
- Can Wireshark capture remote traffic?
- Can Wireshark decrypt HTTPS?
- Can Wireshark capture mobile traffic?
- Can Wireshark send packets?
- Can Wireshark hack Wi-Fi password?
- Can Wireshark block traffic?
- Conclusion
Plain text network protocols
So how is it actually possible that Wireshark can capture passwords? That’s because some network protocols do not use encryption. Such protocols are called clear text (or plain text) protocols. And since clear text protocols do not encrypt the communication, all data are visible to the naked eye, including passwords. Anybody who is in position to see the communication (e.g. man in the middle) can ultimately see everything.
Following table lists some of the most popular clear text protocols still being used today and also some other protocols which allow clear text authentication:
| Port | Service | Name |
| tcp/20, tcp/21 | FTP | File Transfer Protocol |
| tcp/23 | Telnet | Teletype Network Protocol |
| tcp/25 | SMTP | Simple Mail Transfer Protocol |
| tcp/80 | HTTP | Hyper Text Transfer Protocol |
| tcp/110 | POP3 | Post Office Protocol |
| tcp/143 | IMAP4 | Internet Message Access Protocol |
| udp/161, udp/162 | SNMP | Simple Network Management Protocol |
| tcp/389 | LDAP | Lightweight Directory Access Protocol |
| tcp/1080 | SOCKS | SOCKetS Proxy Protocol |
| tcp/1433 | MSSQL | Microsoft SQL Database |
| tcp/5222 | XMPP | Extensible Messaging and Presence Protocol (Jabber) |
| tcp/5432 | PostgreSQL | PostgreSQL Database |
| tcp/6667 | IRC | Internet Relay Chat |
In the following sections we will look closer on these protocols and see examples of captured passwords using Wireshark.
Disclaimer: All screenshots has been redacted and/or modified to protect client data.
Capture FTP password
File Transfer Protocol (FTP) was born in 1971 and it typically uses ports tcp/20, tcp/21. Although it is very old protocol, some organizations still use it today in their networks. FTP is a plain text protocol and therefore a well positioned attacker can capture FTP login credentials very easily using Wireshark. The following screenshot shows example of a captured FTP password using Wireshark:
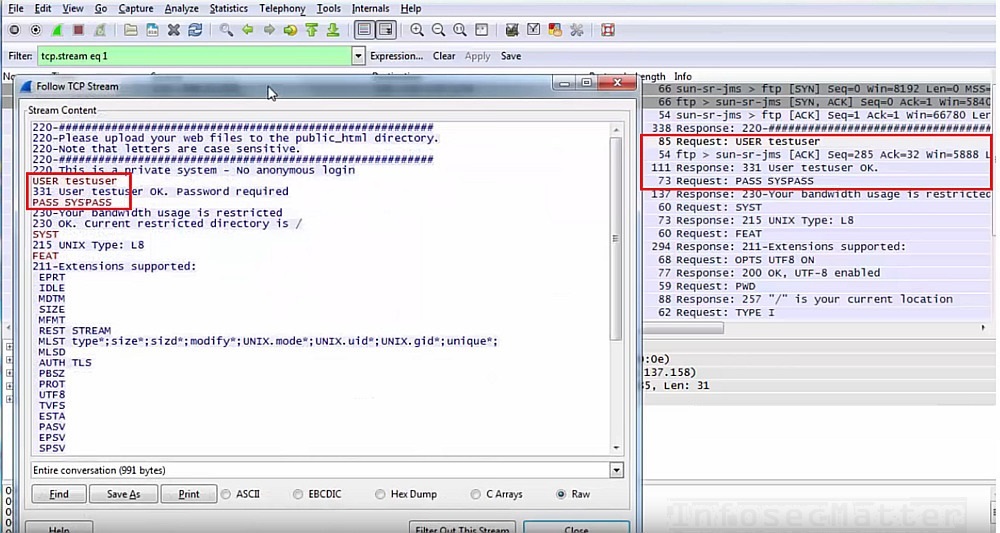
Extract files from FTP using Wireshark
Since FTP is a plain text protocol, we can also capture the actual data being transferred over this protocol. We can extract all the files (e.g. images, documents, audio files etc.) from the network with Wireshark. Brad Duncan from PaloAlto Networks wrote an excellent article describing how to do that.
We could also use Chaosreader to extract the data out from a PCAP file.
Capture Telnet password
Telnet protocol using port tcp/23 certainly needs no introduction. It is used mainly for administration purposes and it is notoriously known for its insecurity. Because there is no encryption, there is no privacy nor protection against eavesdropping. Nevertheless, Telnet is still being used today.
There are many different devices that use telnet as a protocol for administration. For some devices, telnet is the only option without having any alternative (e.g. there is no SSH nor HTTPS web interface available). This makes it very hard for the organizations to get rid of it completely. Telnet can be usually seen on:
- Network equipment (routers, switches..)
- Video conferencing systems (e.g. Cisco TelePresence)
- Access control systems (e.g. access card readers)
- Storage and tape systems
- Printers and imaging devices
- Legacy IP phones
- Mainframes
Since telnet is a plain text protocol, a well positioned adversary can eavesdrop on the communication and capture everything, including passwords. Example of a telnet communication with captured password can be seen in the following screenshot:
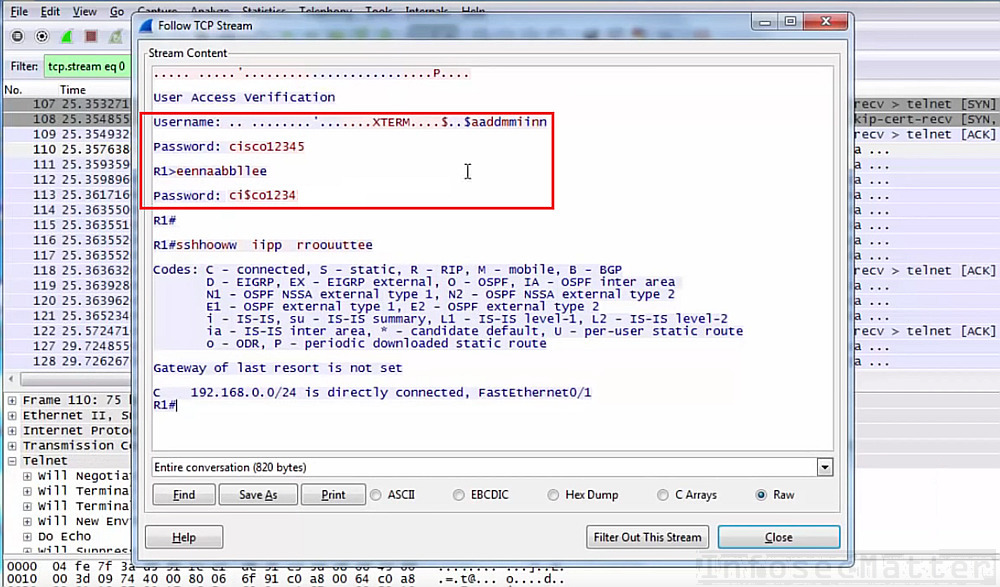
An attacker could now completely overtake the Cisco router.
Capture SMTP password
Simple Mail Transfer Protocol (SMTP) has also been with us for many decades. It uses port tcp/25 and although there is a secure alternative on port tcp/464, the port tcp/25 is open practically on every mail server today due to the backward compatibility.
Most of the servers on port tcp/25 require ‘STARTTLS’ command to initiate the SSL/TLS encryption before any authentication attempts. However, mail servers within some organizations still support plain text authentication over the unencrypted channel. This is mostly due to legacy systems within their internal networks.
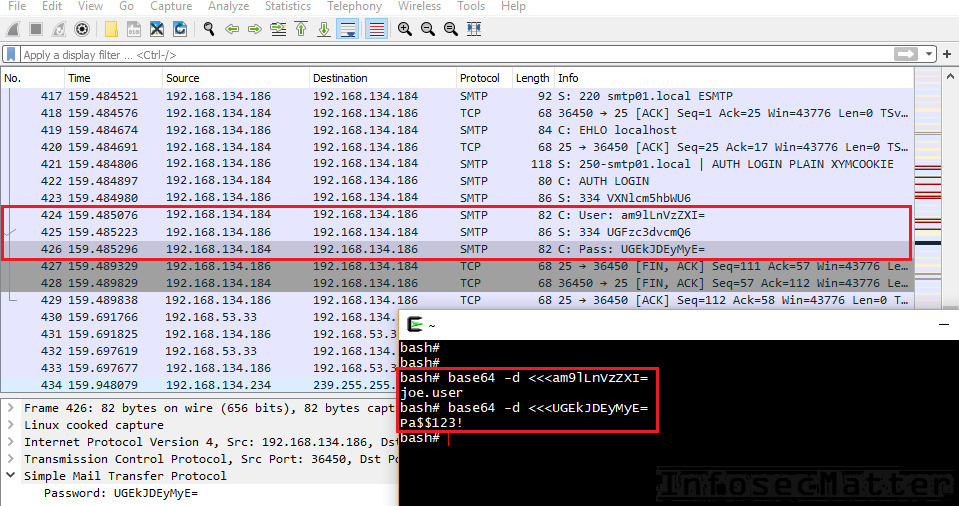
If somebody uses a plain text authentication during SMTP transaction, a well positioned attacker can sniff the credentials. All that the attacker has to do is to base64 decode the username and password. That is because SMTP uses base64 encoding to encode the username and password during the transaction.
In the following screenshot we can see a captured SMTP credentials using Wireshark and consequent base64 decoding using the base64 utility on Linux:
On Windows we could use the certutil.exe command to decode the captured credentials like this:
echo base64encodedstring >file.b64
certutil -decode file.b64 file.txt >NUL
type file.txt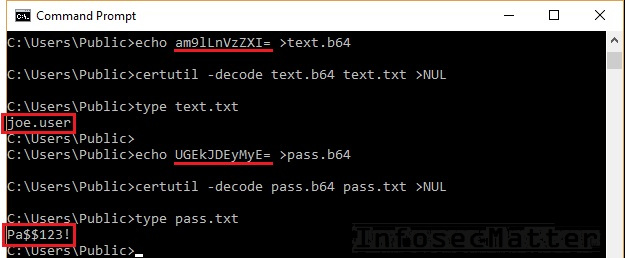
Note that we could also use online tools such as base64decode.org or base64decode.net to do the base64 decoding. But we should be careful with this – perhaps we don’t want to be disclosing private credentials to other parties on the Internet. This is especially important during penetration tests and other offensive exercises, where sensitivity and privacy is crucial.
Capture IMAP4 password
Internet Message Access Protocol (IMAP) is another email related protocol. It uses port tcp/143 and usually requires ‘STARTTLS’ command to initiate the SSL/TLS encryption before any authentication attempts. But similarly as SMTP, some organizations still support ‘plain’ authentication over the unencrypted channel. In such cases the authentication is visible to any well positioned attacker.
The following screenshot shows IMAP credentials captured from the network with Wireshark:
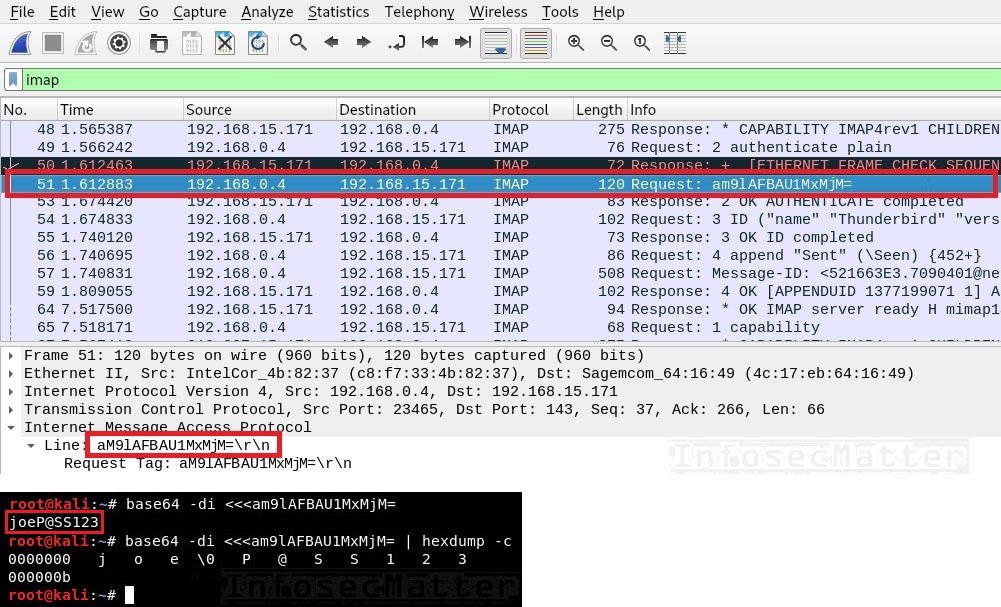
Note that IMAP4 also uses base64 encoding similarly as SMTP. Therefore, is is necessary to decode the captured authentication again to obtain clear text username and password. Notice the NULL byte (\0) between the username and password separating them in the above screenshot.
The attackers could now access joe’s mailbox and read any of his emails.
Capture HTTP password
Hypertext Transfer Protocol (HTTP) surely needs no introduction either. It typically runs on port 80/tcp and since it is a plain text protocol, it offers very little to no privacy to the communicating parties. Anybody who is in position to eavesdrop on the communication can capture everything over this channel, including passwords.
Even though there has been a tremendous effort done by all major browser vendors to discourage usage of HTTP as much as possible, we can still see HTTP being used on internal networks during penetration tests. Here’s an example of login credentials captured in a HTTP communication in a POST request:
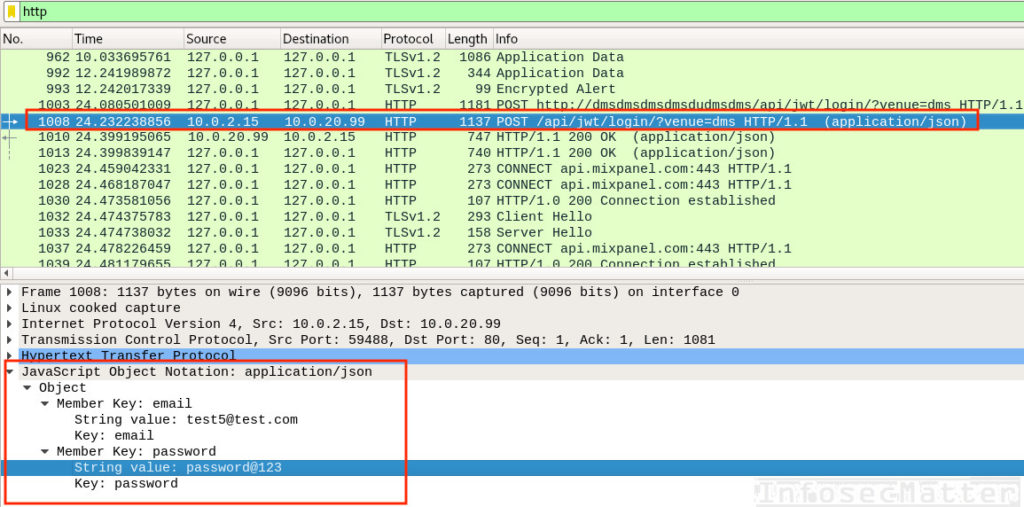
Here’s another example capturing a basic authentication in a HTTP GET request. Note that the authentication string is base64 encoded again, similarly like in SMTP or IMAP4 protocols. But in case of HTTP basic authentication, Wireshark decodes it for us automatically:
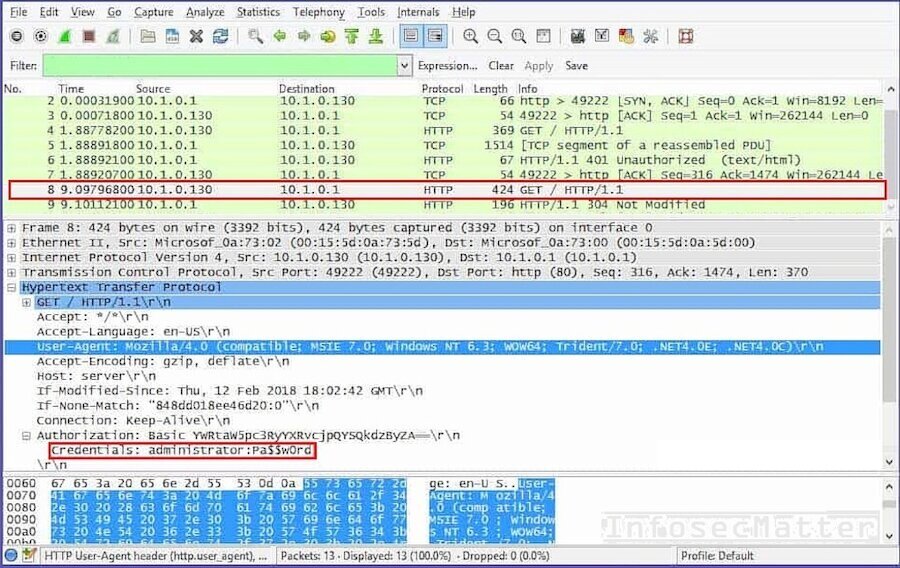
Capture HTTP session cookies
By eavesdropping on the unencrypted HTTP communication, an attacker could also easily capture session cookies with Wireshark. Sniffing a session cookie from the network has practically the same impact as sniffing credentials.
Capture files from HTTP traffic
By using Wireshark we can also easily extract files such as images, documents and audio files from the network traffic. Brad Duncan from PaloAlto Networks wrote an excellent article describing how to extract data from various network protocols using Wireshark. There is also Chaosreader tool which allows to extract data out from a PCAP file.
Capture SNMP community string
Simple Network Management Protocol (SNMP) typically runs on port udp/161. Its primary objective is to manage and monitor network devices and their functions. There are 3 versions of SNMP protocol and the first 2 versions (v1 and v2c) are plain text protocols. SNMP uses something called community string, which is equivalent to authentication. Therefore, capturing SNMP community string is practically the same as capturing credentials.
Although SNMPv3 has been with us for almost 2 decades now, things take time. Most organizations still use v1 or v2c within their internal networks. This is typically due to the backward compatibility with legacy systems in their networks.
Here’s an example of captured SNMP community string using Wireshark:
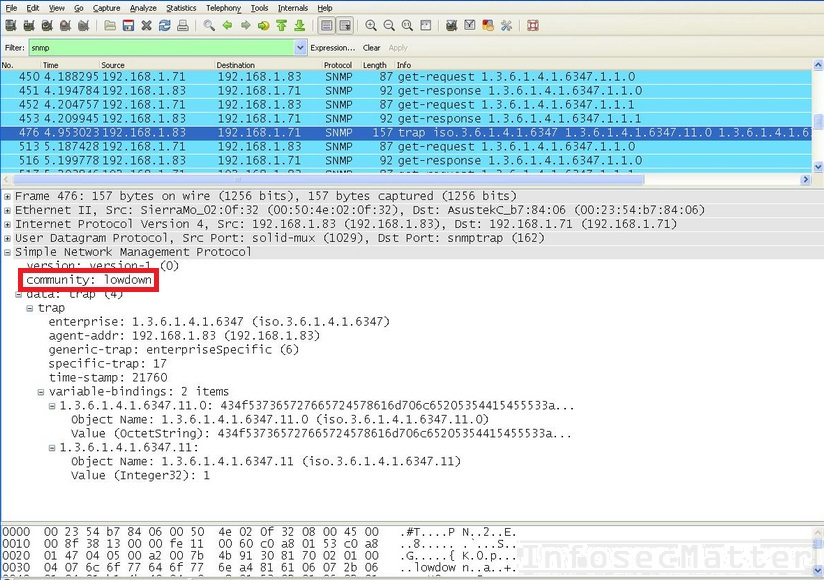
An attacker could now use the community string and gather detailed information about the remote system. This could allow the attacker to learn sensitive details about the system and plot further attacks against it. Note that sometimes the community string also allows to modify configuration on the remote system (read/write access).
Capture LDAP password
Lightweight Directory Access Protocol (LDAP) implements a protocol for accessing and maintaining directory information services. It typically runs on port tcp/389 as plain text service, unencrypted. Therefore it is prone to eavesdropping as any other clear text protocol.
LDAP can use multiple authentication methods. The most basic method is called ‘simple’ and it is essentially username and password in clear text. Therefore, anyone who is in position to inspect the network traffic can capture LDAP simple authentication very easily.
Here’s an example of LDAP authentication captured with Wireshark:
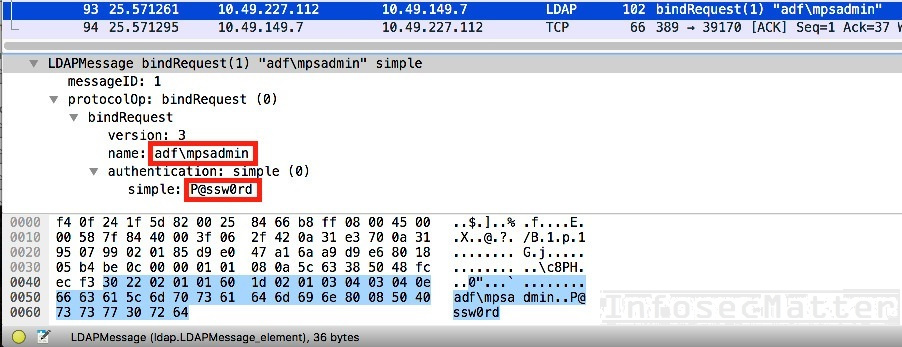
Furthermore, in Windows Active Directory environments, domain controllers are usually exposing LDAP interface on port tcp/389. Typically there are some systems in the network integrated with the Active Directory using the LDAP interface – e.g. attendance systems, access control systems, printers etc. In such cases, these systems could allow an attacker to capture valid domain user credentials via LDAP, if they are not properly secured. See an example here from one of our pentests.
Capture SOCKS password
SOCKS is very versatile and popular proxy protocol, which allows to forward (or tunnel) any TCP or UDP traffic between the client and the server. SOCKS version 5 also supports authentication. Since SOCKS doesn’t do any encryption on its own, all data going through the tunnel goes “as is”. On top of it, if we are in position to capture network traffic between the client and the server, we can capture the SOCKS authentication as well.
The SOCKS5 protocol supports multiple authentication methods. One of them is username and password and since there is no encryption, a well positioned attacker can capture it using a packet sniffer.
Following screenshot shows example of SOCKS5 authentication captured using Wireshark:
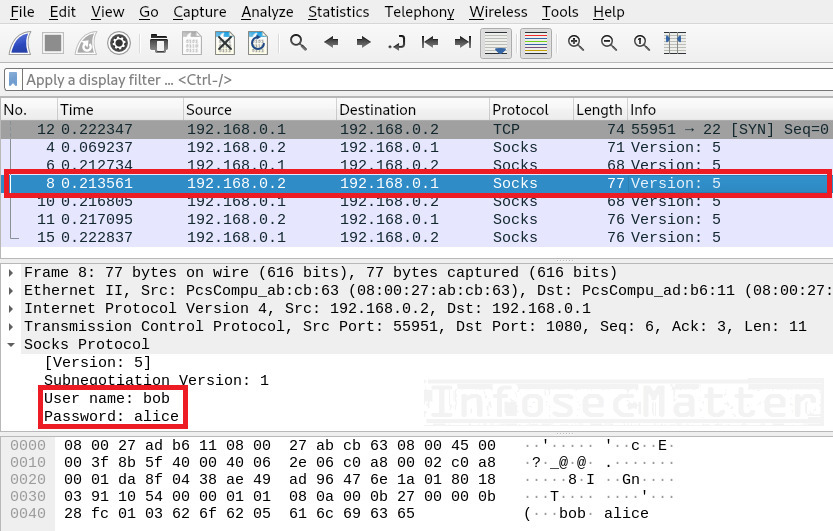
An attacker could now use the SOCKS proxy server and access systems on the server side network.
Capture MSSQL password
Microsoft SQL server typically runs on port tcp/1433 and it is yet another service for which we can capture password with Wireshark. If the server is not configured with ‘ForceEncryption’ option, it is possible to capture plain text authentication either directly or by using a downgrade attack. A man-in-the-middle could capture MSSQL credentials very easily.
Here’s an example of captured MSSQL password of the ‘sa’ user using Wireshark:
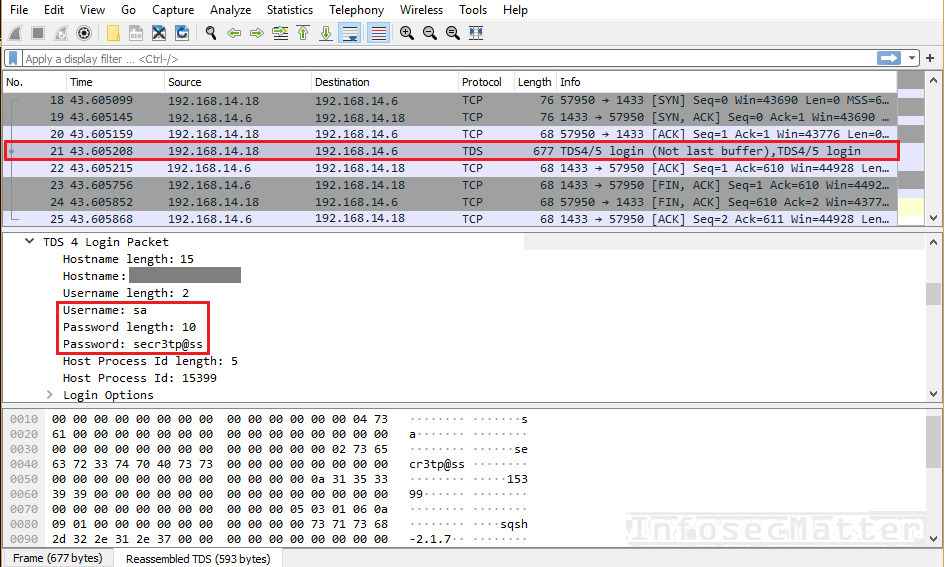
Note that in MSSQL the ‘sa’ user is the System Administrator account – the highest privileged user. Therefore, this would have a critical impact allowing the attacker to take complete control over the database server. It could also lead to a remote command execution (RCE) via the xp_cmdshell functionality (link, link, link..).
Capture PostgreSQL password
PostgreSQL is another very popular SQL database server. It runs on port tcp/5432 and it supports variety of authentication methods. Usually it is configured to disallow clear text authentication, but sometimes it is configured to allow it. In such cases a well positioned attacker could capture the username and password by eavesdropping on the network traffic.
Note that the PostgreSQL authentication comes in multiple packets. First there is the username and the database name:
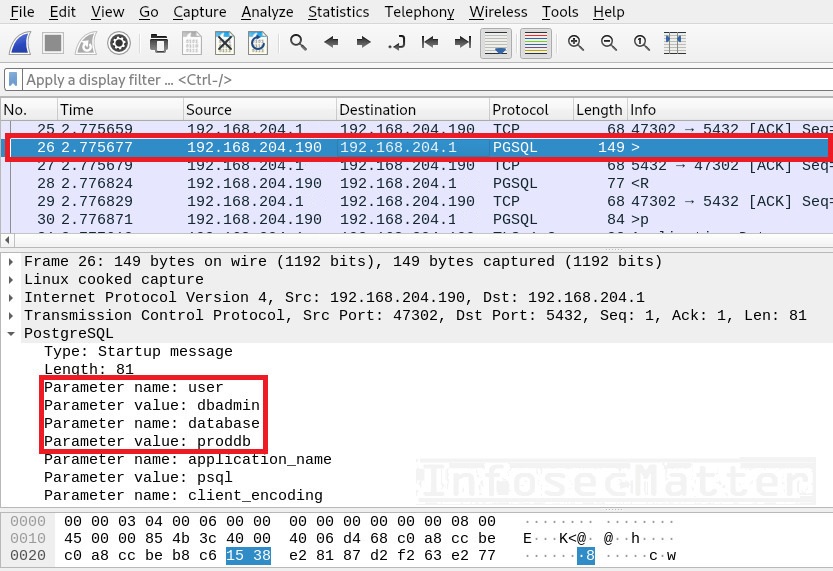
In consequent network packet, we can see the PostgreSQL password as well:
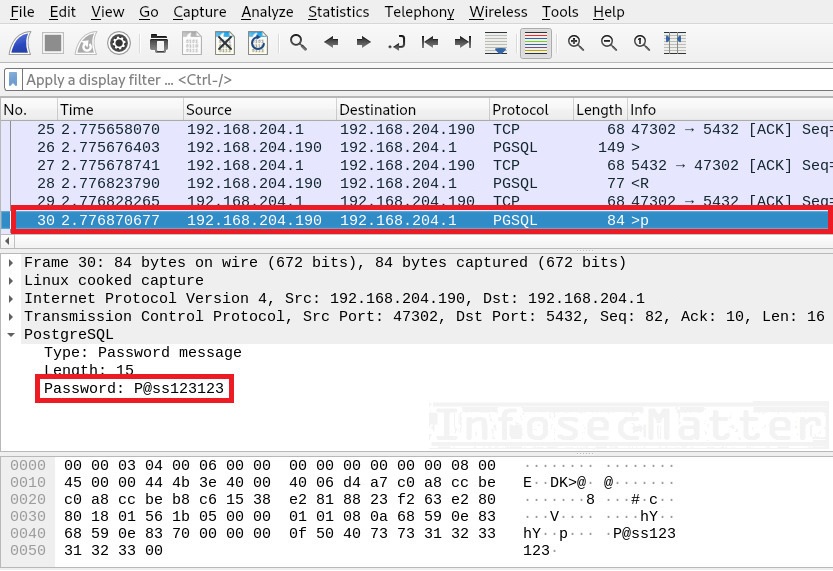
Capture IRC password
Internet Relay Chat (IRC) is a chat protocol typically using port tcp/6667. IRC used to be very popular back in the 90s. Although it is not so popular any more today, some people still use it and it is still around. Furthermore, malware writers and botnet operators use it as well to manage their armies of bots. They typically have a private IRC server protected by a password or a private channel (chat room) somewhere on a public IRC server.
Since IRC is a clear text protocol, it is very easy to capture credentials transmitted over this channel. Here’s an example of IRC password captured with Wireshark:
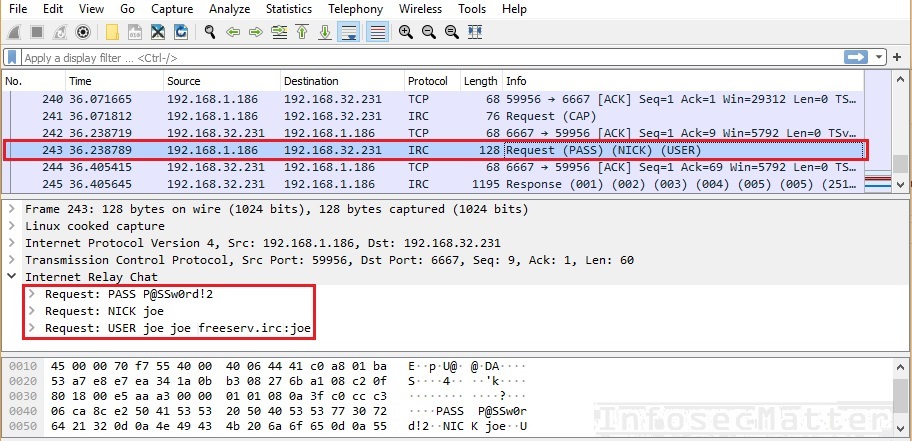
With those credentials we could now connect to the password protected IRC server.
Capture OSPF password
Open Shortest Path First (OSPF) is a routing protocol for IP based networks. The most common is OSPF version 2, which was specified in 1998. This protocol is typically used in very large networks and on backbone networks of various service providers (e.g. ISP).
OSPF supports multiple authentication methods and one of them is plain text. In such case, a well positioned attacker who can eavesdrop on the communication can sniff the OSPF password from the network using Wireshark:
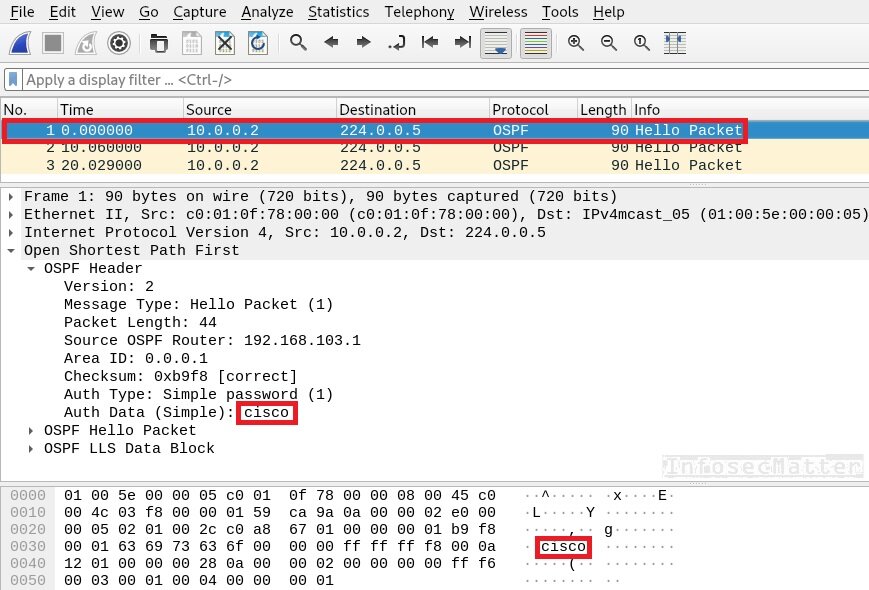
An attacker could now send false route advertisements, redirect network traffic flows or disrupt provided services (connectivity).
Capture BFD password
Bidirectional Forwarding Detection (BFD) protocol specified in 2010 is used to provide diagnostic information between two connected systems. It is usually used together with routing protocols such as BGP or OSPF to quickly detect faults on the link. This protocol is typically used in very large networks and on backbone networks of various service providers (e.g. ISP).
The BFD protocol supports multiple authentication methods and one of them is also plain text. In such case, a well positioned attacker who can eavesdrop on the communication can sniff the BFD password from the network with Wireshark:
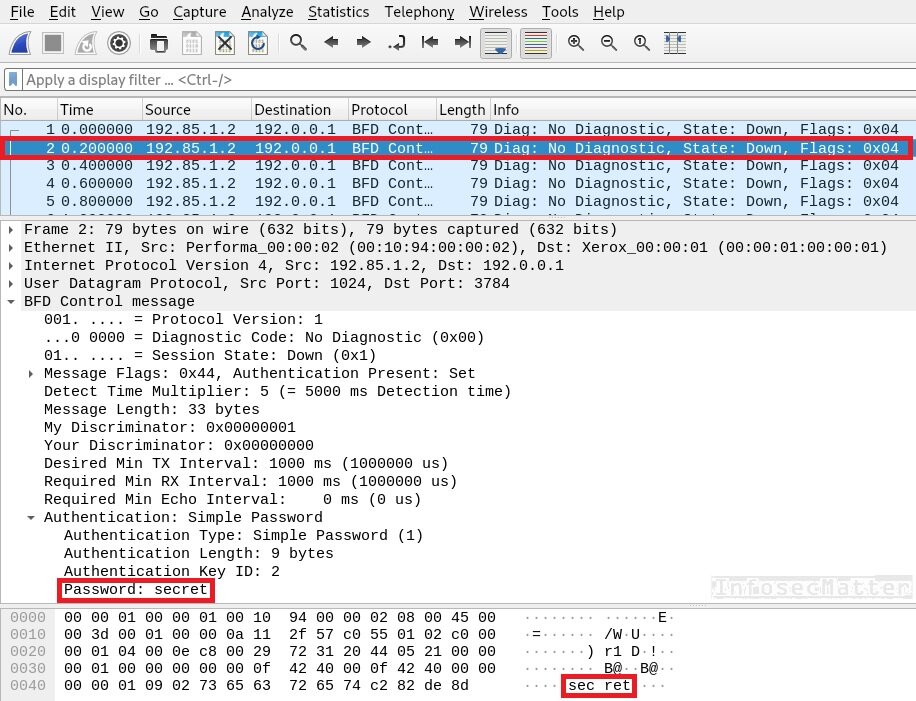
An attacker could now send false diagnostic information and potentially disrupt the services.
Capture STUN authentication
Session Traversal Utilities for NAT (STUN) specified in 2003 is a set of methods for performing NAT traversal. It is typically used by various real-time audio, video, messaging and other interactive communication systems (e.g. VoIP telephony). A well positioned attacker could easily sniff the STUN password using Wireshark.
Here’s an example of captured STUN authentication using Wireshark:
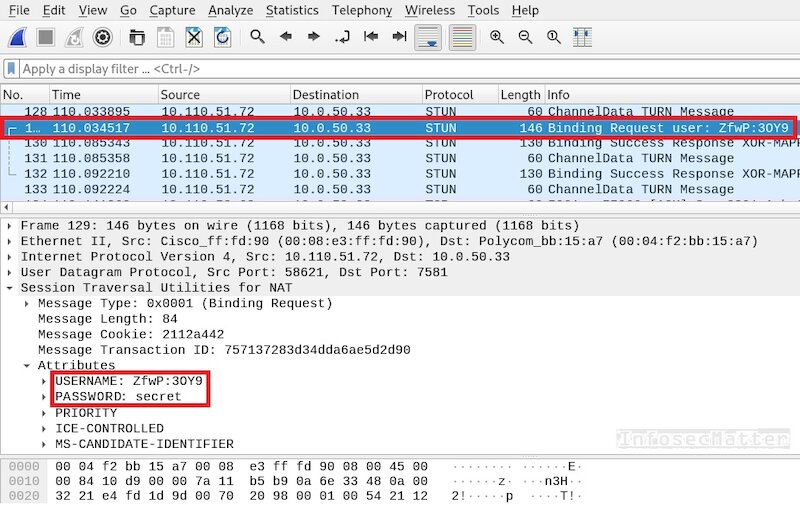
An attacker could now perform NAT traversal and potentially create channels to access internal systems from the outside.
Better approach to capture passwords
While capturing passwords with Wireshark may look effective, during penetration tests it is not very practical. It is because we have to inspect every packet with our own eyes to find the passwords.
Much better approach is to record the network traffic into PCAP file using Wireshark (or Tcpdump, Dumpcap, Tshark or similar tool) and then process the PCAP file offline with automated tools such as Ngrep, Ettercap or others.
Let’s have a look on some..
Capture passwords with Ngrep
Ngrep (network grep) is one of our favorite tools when it comes to quick network analysis. It is like the grep program (or findstr.exe program on Windows), but for the network layer. Ngrep allows to search through network traffic and match for any kind of string or pattern. It supports regular expressions and also hexadecimal expressions (binary strings). Ngrep was written by Jordan Ritter.
This is how we can use Ngrep to search through a PCAP file:
ngrep -I file.pcap -q -i "pattern"- -I (read PCAP file)
- -q (quiet mode)
- -i (case insensitive match)
This is how we can sniff passwords with Ngrep from a PCAP file:
ngrep -I file.pcap -q -i ‘pass=|pwd=|log=|login=|user=|username=|pw=|passw=|passwd=|password=|pass:|user:|username:|password:|login:|pass |user |auth'Here’s another example of using Ngrep with more regex-ish pattern borrowed from here:
ngrep -I file.pcap -q -i ‘[&\s?](?:login|user(?:name|)|p(ass(?:word|wd|)|w|wd))[\s:=]\s?([^&\s]*)'Although Ngrep is very powerful, it is not the ultimate solution for capturing passwords. Not every network protocol uses an easily match-able authentication format (e.g. username=something or password=something etc.). Furthermore, we will also likely get a lot of noise (false positives) with our patterns. In the end of the day, we would not be able to match all the passwords that we captured above with Wireshark.
Capture passwords with Ettercap
Ettercap project is another tool that we can use for capturing passwords. It is a comprehensive suite for man-in-the-middle attacks and It was specifically designed for sniffing passwords out of the network traffic. Ettercap was originally written by Alberto Ornaghi and Marco Valleri.
Ettercap supports a whole range of network protocols and not just the plain text ones – it supports also variety of binary network protocols. It can recognize many authentication methods and it can sniff out not only passwords, but also password hashes which can be consequently cracked with hashcat, john the ripper or similar tool.
This is how we can sniff passwords with Ettercap from a PCAP file:
ettercap -T -q -r file.pcap- -T (text only interface)
- -q (quiet mode)
- -r (read PCAP file)
Ettercap will automatically detect interesting parts of the packets – there’s no need to provide any additional arguments to it. Here’s an example of captured PostgreSQL password using Ettercap:
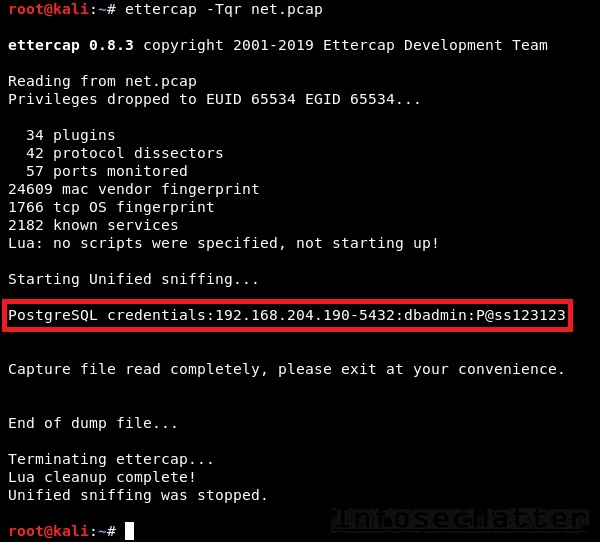
Unfortunately, our experience is that Ettercap sometimes fails to recognize credentials. This is also true with the latest version (0.8.3) of Ettercap, unfortunately. On the other hand, no other tool is able to recognize hashes and output them in a crack friendly format to crack them with john the ripper, for instance.
Capture passwords with Tshark
Tshark is probably the best solution to capture passwords from the network in an automated way. Even though it can produce a lot of noise, Tshark will be the least likely to miss something, because it uses the same libraries and dissectors as Wireshark does. That means an unparalleled number of supported protocols.
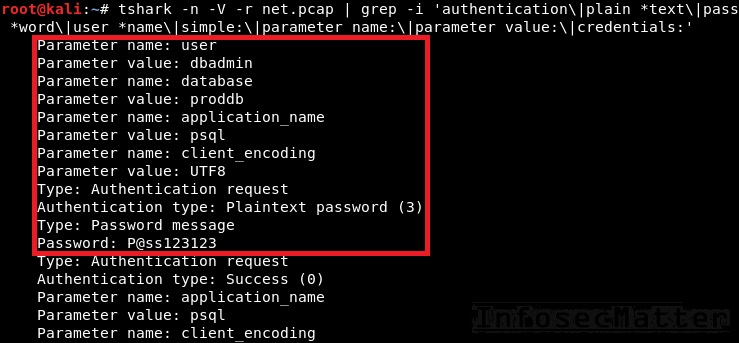
This is how we can sniff passwords with Tshark from a PCAP file. We simply pipe it to the grep command and look for patterns associated with authentication:
tshark -n -V -r file.pcap | grep -i 'authentication\|plain *text\|pass *word\|user *name\|simple:\|parameter name:\|parameter value:\|credentials:'- -n (disable name resolving)
- -V (verbose mode / expand all packet fields)
- -r (read PCAP file)
Here’s an example of the same captured PostgreSQL password, but this time using Tshark:
Frequenty asked questions (FAQ)
This section provides answers to some of the frequently asked questions when it comes to capturing network traffic with Wireshark. Most of these are applicable to any packet sniffer.
Can Wireshark be detected?
In most cases no. Running a fully passive packet sniffer cannot be detected since it is only passively listening on the network. But in certain circumstances it can be detected and this is applicable to every packet sniffer. There is a technique to detect packet sniffer which works only if the sniffing host:
- is on the same local network
- does not have a firewall rule that blocks incoming ICMP packets
- does the sniffing with an interface that has TCP/IP enabled, and thus is able to reply to an incoming ICMP packet
The method works by sending an ICMP ping packet to the sniffing host with an incorrect destination MAC address. The sniffing host will receive it and the operating system will respond to it despite the fact that it is not addressed to it. There is an Nmap script for this method available here.
Is Wireshark safe to use?
Yes, Wireshark is generally safe to use. However, keep in mind that it is a software as any other and so it may contain vulnerabilities. See the full list of Wireshark vulnerabilities on this page. Always use the latest version from the official website to minimize any potential risk.
Can Wireshark capture packets from other computers?
Yes it can. As long as the packets from other computers are arriving to our network interface, Wireshark will be definitely able to capture them. This is because it is running in a promiscuous mode and therefore it is capturing everything that arrives to it.
But the question is what will arrive to us? This is very much dependent on our logical position in the network. Are we running Wireshark on a router (gateway)? Are we on a wireless network? Are we on a switched network? Are we capturing traffic from a SPAN port? It simply all depends.
Can Wireshark capture remote traffic?
Generally speaking, we can only capture traffic that is coming to our network interface. Thus, we cannot sniff traffic directly from a remote system. But with some help we can actually do that. The following options are available to capture remote traffic with Wireshark:
- Remote Packet Capture Protocol which allows to capture traffic from remote Windows or Linux systems (link)
- Running tcpdump over SSH and Wireshark receiving traffic from it using a pipe (link)
- Cisco Remote Capture protocol which allows to capture network traffic from a remote Cisco device (link)
- Configuring mirror or SPAN port (link)
Can Wireshark decrypt HTTPS?
Yes, Wireshark can decrypt HTTPS SSL/TLS encrypted traffic as long as it has the private keys. Wireshark can decrypt SSL and TLS using a pre-master secret key method. Another method is to use an RSA key to decrypt SSL, but this deprecated method. Both of these methods require Wireshark to have access to the private keys for it to be able to decrypt the HTTPS traffic.
Detailed steps on how to do this on Windows, Linux or Mac systems can be found here.
Can Wireshark capture mobile traffic?
Yes, Wireshark has a number of dissectors that can analyze mobile traffic going over the mobile phone network (e.g. GSM). In order for this to work, Wireshark needs to be able to receive the mobile traffic using a special equipment such as OsmocomBB compatible phone, for instance.
More information on this can be found here.
Can Wireshark send packets?
No, Wireshark cannot send packets. Wireshark can only capture packets and analyze them. It does not have any capability to generate packets or inject packets to the network. Wireshark is only a packet analyzer. This applies also to Tcpdump and Tshark.
For packet injection or packet crafting see projects such as hping, Scappy, Ostinato or others.
Can Wireshark hack Wi-Fi password?
The short answer is most likely no. it is not possible to hack Wi-Fi password using Wireshark. No matter how the wireless network is configured or which encryption is used, it is probably not possible to capture Wi-Fi password using Wireshark.
The only possible scenario where Wireshark could capture Wi-Fi password would be a scenario of an open, unencrypted wireless network with an insecure captive portal running on HTTP.
Open Wi-Fi with an insecure captive portal
Suppose we are in vicinity of an open, unencrypted Wi-Fi and there is a captive portal in place for getting access to the Internet. Since the Wi-Fi is open and unencrypted, we can capture all packets from the air. Chances are that someone in our vicinity will be authenticating to the captive portal at some point. Now if the captive portal is running over unencrypted channel (HTTP), we will be able to sniff the credentials to the captive portal.
In other cases where encryption is used (WEP, WPA, WPA2, WPA3 etc.), Wireshark would be of little help to get on the network. There are other tools designated to gain access to such wireless networks, namely Aircrack-ng suite.
Can Wireshark block traffic?
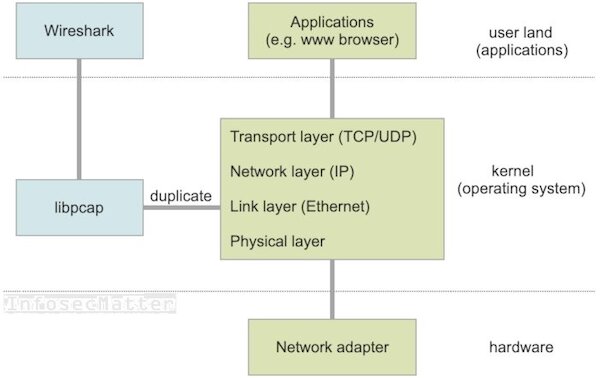
No, Wireshark cannot block network traffic. Wireshark doesn’t have any firewall or packet blocking capabilities. It cannot modify the packets in any direction and in any capacity. Wireshark can simply only capture packets, dissect them and analyze them.
The way that Wireshark works is that the network packets coming to and from the network interface are duplicated and their copy is sent to the Wireshark. Wireshark does not have any capacity to stop them in any way – the original packets will still be processed by the operating system and consequently passed on to the processes and applications expecting them.
See the following diagram showing how Wireshark works:
Creating firewall rules with Wireshark
Although Wireshark cannot block the network communication, it can help us construct firewall rules for our firewall. Based on the traffic that we are looking at, Wireshark can generate firewall rule for it. All we have to do is simply select the packet that we want to block and navigate in the menu:
- Tools -> Firewall ACL Rules
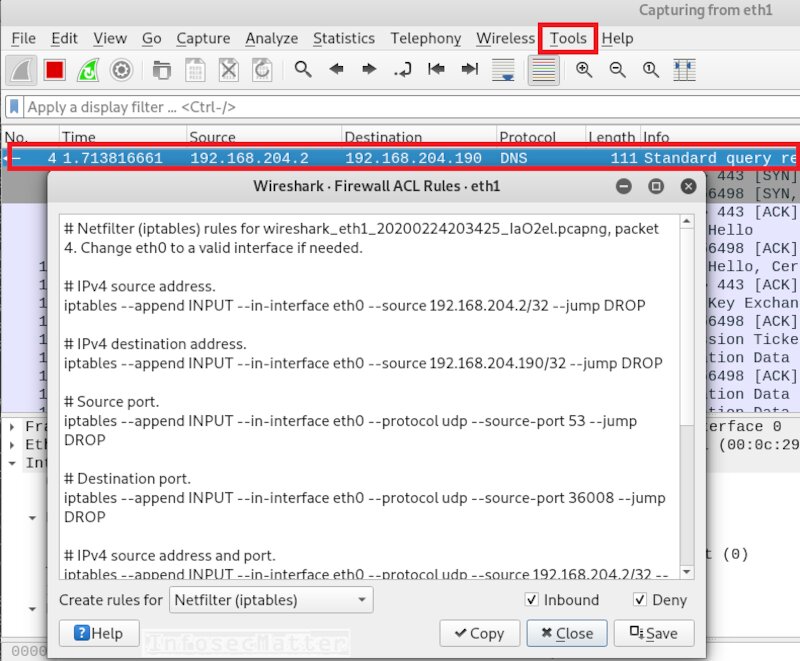
We can now copy paste selected rules directly to our firewall. Wireshark supports syntax of the following firewalls:
- Cisco IOS (standard / extended)
- IP Filter (ipfilter)
- IPFirewall (ipfw)
- Netfilter (iptables)
- Packet Filter (pf)
- Windows Firewall (netsh)
Conclusion
There are many network protocols for which we can capture authentication with Wireshark. As long as we are in position to eavesdrop on the network communication and as long as the communication is unencrypted, there is a risk. A well positioned attacker can capture not only passwords, but literally any kind of information passing by on the network.
If you like this information and you would like more, please subscribe to our mailing list and follow us on Twitter and Facebook to get notifications about new content.
SHARE THIS




















Excellent article. The article actually shows your dedication and hard work, and passion for your work. No doubt, the article contains a lot of information, and at the same time, identify the loopholes, that these protocols have. That at one end is severe, because people are today, quite concerned about their privacy. And that includes been some quite private information as well.
You are absolutely correct, Katie. Thanks for stopping by and your kind words.