Tor is the number one choice for millions of Internet users when it comes to anonymous and private communication on the Internet. This article aims to address some of the most common concerns that users have with regards to their privacy and anonymity. Can “The Onion Router” be really trusted?
- Will Tor browser hide my IP?
- Can you be tracked on Tor?
- Does Tor leave anything on your computer?
- Where is Tor browser cache?
- Can Tor browser access blocked sites?
- Can Tor browser be traced?
- Does my ISP know if I am using Tor?
- Does my ISP know what sites I visit when I use Tor?
- Can Tor browser be blocked?
- Conclusion
Let’s jump right to it..
Will Tor browser hide my IP?
Yes, by using Tor you will effectively hide your real IP address on the Internet. All your communication will go encrypted through at least three random servers (also known as relays) before reaching the destination. This makes it virtually impossible for anyone to find out your real IP address.
Although there are some techniques on how to reveal someone’s real IP address behind Tor, you can minimize most of the risk by using the official Tor Browser. The official Tor Browser by default blocks usage of dangerous plugins and add-ons such as Flash Player for instance, which could be manipulated into revealing your real IP address. You can of course always enable Flash Player if you choose to, but with the official Tor Browser your privacy is protected by default.
The list of known Tor weaknesses can be found on the Wikipedia. But despite all the weaknesses, Tor is still considered to be one of the most resilient anonymity networks providing very strong protection against traffic analysis and source IP address disclosure.
Can you be tracked on Tor?
No, you cannot be tracked when you are using Tor. The Tor Browser by default blocks all analytics trackers and advertising beacons, which could link your activity across different sites. Unless you explicitly allow yourself to be tracked, you should be safe using Tor.
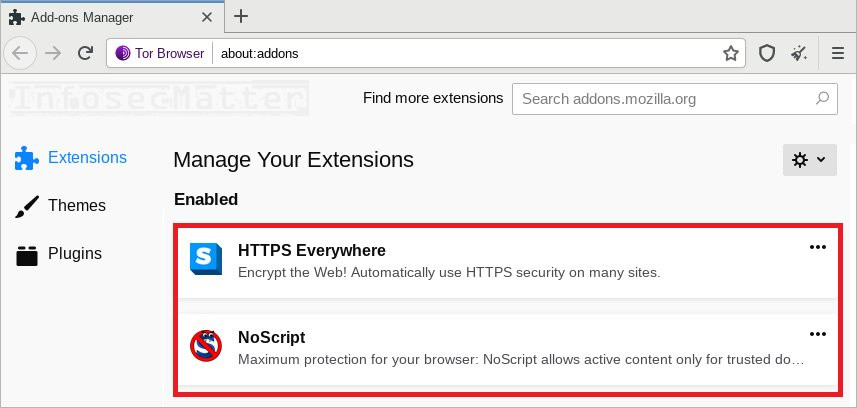
As the first line of defense, Tor Browser comes pre-installed with the following two add-ons:
- NoScript add-on
- blocks any third-party scripts from running in your browsing session
- blocks advertisement sites, analytical trackers and others
- allows active content only for trusted domains that you choose
- HTTPS Everywhere add-on
- automatically switches browsing to all websites from insecure HTTP to secure HTTPS
- ensures that all your communication is going through SSL/TLS encrypted channels (HTTPS)
- displays warning of any attempts browsing a website using insecure HTTP communication channel
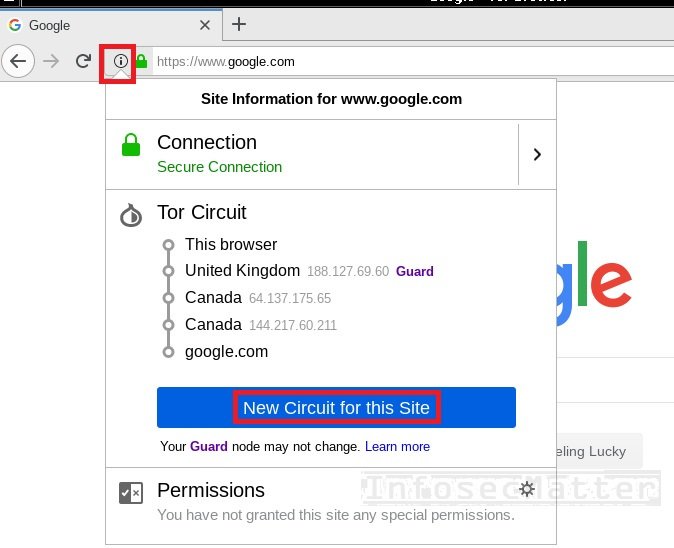
By using the Tor network, you effectively disallow observers on the Internet to see your exact location and IP address. But even without this information, the services that you are using (the websites that you are visiting) could still link together some of your activities, e.g. by observing cookies that your browser is sending or by observing your exit node’s IP address. For this reason, Tor Browser also contains the following two additional features:
- New Tor Circuit for this Site button
- forces the Tor Browser to establish a new circuit within the Tor network
- immediately changes your exit node’s IP address
- protects your unique session source IP address
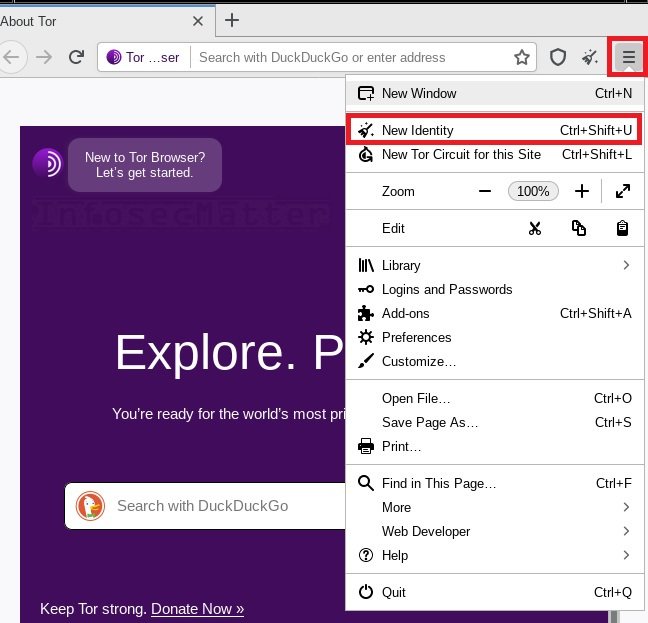
- New Identity button
- restarts the Tor Browser, effectively resetting all web sessions
- erases all session cookies and purges all cache from memory
- protects your unique session identify
Does Tor leave anything on your computer?
No, Tor does not leave any information on your computer. The Tor Browser does not keep any browser history, it does not cache on disk nor it stores session cookies anywhere on the disk. It is designed with the utmost privacy and confidentiality in mind to protect its users.
Even after a long browsing session, there should no trails left on your computer. If there were any trails left, it would be a major bug. The project community takes these kinds of defects very seriously. They even have a specific keyword (tag) for these issues called tbb-disk-leak. You can see all such defects being tracked here:
Furthermore, to avoid storing anything on the disk is one of the core design requirements of the Tor Browser. See more information in the “Disk Avoidance” section here:
Where is Tor browser cache?
There is no cache. All content caching is disabled in the Tor Browser by default. The Tor Browser is designed to keep all browsing data (browser history, cache, session cookies) in memory without storing anything on the disk. This is one of the core design features of the Tor Browser.
For more information about this, see the following link:
Can Tor browser access blocked sites?
Yes, the Tor Browser allows users to access blocked websites. Regardless of whether it is a geo-restricted website or a censored website, using the Tor network allows users to circumvent these restrictions and access virtually any blocked or censored website anonymously and privately.
This is because the Tor network uses a large number of interconnected nodes (relays) around the globe connected to the Internet. It allows the users to hide their real IP address and appear as if they are coming from somewhere else. This in most cases will circumvent the censorship or the blockage.
Can Tor browser be traced?
If the Tor Browser is used safely, there is no way to trace back any activity that you do on the Internet while you are using Tor. This includes your ISP. The Tor Browser was specifically designed to disallow anyone to track what Tor users are doing on the Internet.
While this is true in general, there are known techniques and attacks against Tor users that could lead to a privacy leak. This is mostly the case of improper usage of the Tor network. Such cases include for instance:
- Usage of dangerous browser plugins and add-ons
- Accepting insecure connections and ignoring certificate warnings
- Connecting to insecure plain text (HTTP) websites
For instance, some organizations (e.g. schools or companies) force their users to access the Internet through a proxy with SSL inspection. This is also called HTTPS inspection. Connecting to Tor network through such proxy would result in a total loss of privacy and you should never do that. Fortunately, the Tor Browser will warn you in cases like this (certificate warning).
Does my ISP know if I am using Tor?
Yes, your ISP may know if you are using Tor. This is because the list of Tor nodes (relays) is publicly known information due to the fact that some organizations and individuals track them for various reasons. Your ISP may be therefore able identify if you are using Tor.
For instance here you can find the current list of nodes. The list contains thousands of IP addresses and it is updated practically every couple of minutes. Anyone can use this information, including your ISP. All the ISP has to do is to see which IP addresses you are connecting to and if some of those IP addresses are on the list, then your ISP will know that you are using Tor.
But don’t panic. While your ISP can find out if you are using Tor or not, there is no way for the ISP or anyone for that matter to find out what you are doing on the Internet. Nobody can see what websites you are visiting nor where you are connecting to, because everything is encrypted using strong encryption (TLS 1.2 or better).
Does my ISP know what sites I visit when I use Tor?
No, your ISP has no way of knowing what you are doing on the Internet while you are using Tor. The Tor network was specifically designed to prevent anyone (including ISPs) from identifying any particular user on the network or finding out what websites anyone visits while using Tor.
This is due to the way how Tor network works. It was designed to facilitate a true end-to-end anonymity and privacy for its users. It uses only secure HTTPS encrypted channels for entering the Tor network and for communicating within the Tor network as well. Every request goes through at least three random servers (relays) before exiting the Tor network. This makes it virtually impossible to find out what anyone is doing on the network.
This also includes the DNS traffic which means that even the DNS requests are handled within the Tor network. The only thing that your ISP can ever see is a bunch of TLS encrypted connections. This absolutely and totally prevents the ISP from knowing anything about what you are doing on the web.
The following screenshot shows a sample Tor communication captured in Wireshark packet analyzer:
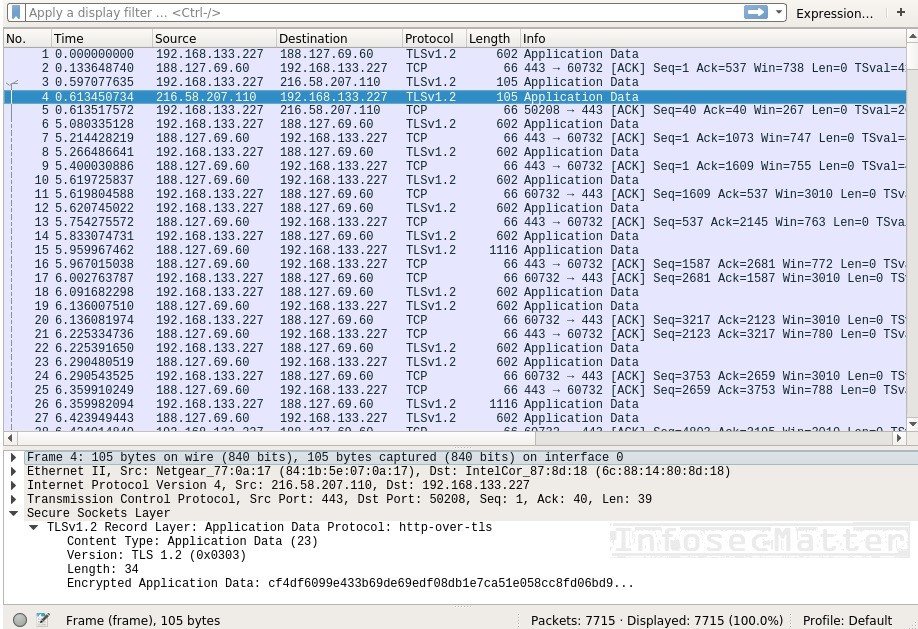
As you can see, there is really nothing much to see..
Can Tor browser be blocked?
It is only partially possible to block Tor. Since Tor is an open network where anyone can connect to, it is equally possible for anyone to get list of Tor relays and put them on a blacklist. In fact there are ISPs, organizations or even countries that do this.
For an ISP, it is very easy to find out whether someone in their network is using Tor. As we mentioned earlier, the list of Tor nodes is publicly available online for anyone to see. Thus, blocking of Tor is not hard and many network devices have this feature built-in (e.g. Fortinet, Palo Alto or Check Point). But as a countermeasure, Tor project community came up with the concept of bridges.
Bridge is essentially a Tor relay with the difference that it is not announced nor listed publicly anywhere on the Internet. Bridges are typically run by volunteers and their addresses can be requested individually on adhoc basis. More information about bridges can be found here:
Conclusion
The Tor network remains to be the top choice for anyone seeking privacy and anonymity on the Internet. As the number of its users constantly rises, so are the new emerging tactics trying to block it or break its security features. The project community, however, keeps evolving with it and constantly improves its robustness and resiliency.
SHARE THIS