Exploits, Vulnerabilities and Payloads: Practical Introduction
As penetration testers, we have to use exploits very often to demonstrate vulnerabilities to our customers. But where do we get them? How do we use them? And what should we keep in mind when using them? Exploits are dangerous ...
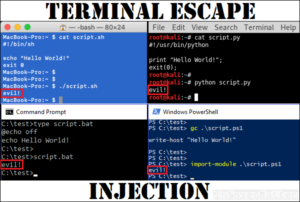
Terminal Escape Injection
As information security professionals, we have to deal with potentially dangerous files practically on daily basis. We run various scripts, PoC code, exploits and other things and we put trust in the utilities that read those files. Can we really ...

Firebird Database Exploitation
During penetration tests, we sometimes encounter a Firebird database installation running on the network. It typically runs on port tcp/3050 and often times it is configured with default credentials SYSDBA/masterkey. What can we do with this? Can we get a ...
