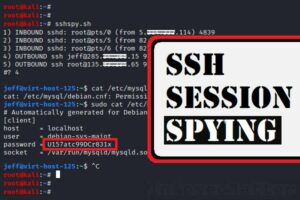
SSH Sniffing (SSH Spying) Methods and Defense
It is well known that SSH is a secure network protocol, inherently safe from network packet sniffing and eavesdropping. This is of course thanks to its use of encryption. If we are using SSH protocol safely, the risks of man-in-the-middle ...
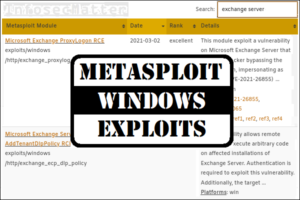
List of Metasploit Windows Exploits (Detailed Spreadsheet)
On this page you will find a comprehensive list of all Metasploit Windows exploits that are currently available in the open source version of the Metasploit Framework, the number one penetration testing platform. It is my hope that this list ...
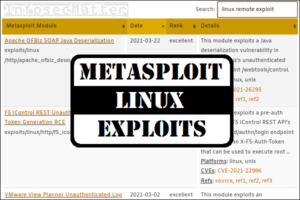
List of Metasploit Linux Exploits (Detailed Spreadsheet)
On this page you will find a comprehensive list of all Metasploit Linux exploits that are currently available in the open source version of the Metasploit Framework, the number one penetration testing platform. It is my hope that this list ...

Spaces in Passwords – Good or a Bad Idea?
In this article we are going to demystify and answer one very important question when it comes to passwords. There are many people who are wondering whether it is a good idea to use spaces in passwords or not. If ...
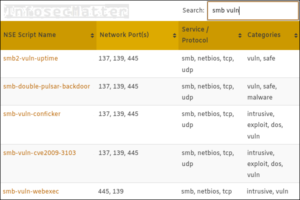
Nmap NSE Library
If you are looking to explore the world of NSE (Nmap Scripting Language) scripts, this page will hopefully help you find what you are looking for, quickly and effectively. On this page you will find a comprehensive list of all ...










